Using NIST CSF 2.0 for SMEs

As a security engineer with some experience in GRC, even though it is not my primary focus in my day to day work, I believe that some cybersecurity frameworks knowledge helps security engineers take a step back and better prioritize their efforts. Today, I would like to present the NIST Cybersecurity Framework (CSF) 2.0 as one of the most widely used frameworks.
Whether you’re new to the CSF or have been using it for years, this overview will walk you through what it encompasses, its recent update, and how you can leverage it to enhance your organization’s cybersecurity.
What Is the NIST Cybersecurity Framework?
First released in 2014, with a minor update in 2018 (v1.1), and a more recent major update in 2024 (v2.0), the NIST CSF was originally created to secure U.S. critical infrastructure. However, its comprehensive and adaptable structure has made it spread across industries, providing organizations with a flexible roadmap for identifying, managing, and mitigating cybersecurity risks. CSF doesn’t impose strict procedures.
Key Components of the CSF
The NIST CSF has three main components: Core, Implementation Tiers, and Profiles. These are used to determine the necessary actions (Core with its security controls), assess the maturity of their security practices (Tiers determining the maturity), and document both current and target cybersecurity capabilities (Profiles).
- The Core: This is the heart of the CSF, organizing cybersecurity into a hierarchy of functions, categories, and subcategories. Originally consisting of five main functions: Identify, Protect, Detect, Respond, and Recover it now includes a new sixth function, Govern, which broadens the framework’s focus on governance and accountability.
- Implementation Tiers: Tiers help measure the maturity and rigor of your organization’s cybersecurity practices, from initial (reactive) to adaptive (proactive), indicating how well you manage risk.
- Profiles: Profiles document an organization’s current cybersecurity capabilities in each category of the Core and set goals for future improvements, offering a way to capture and communicate progress to the different stakeholders.
What’s New in CSF 2.0?
First, the new Govern function focuses on cybersecurity governance, covering risk management, roles, policies, and oversight. The document structure is simpler, with separate resources for quick-start guides and examples. The categories have been reduced from 23 to 22. Finally, NIST has added more resources, including , along with a tool to compare the framework to other standards.
The CSF Core
In CSF 2.0, the six core functions create a holistic approach:
- Identify: Know your assets and potential risks to ensure a comprehensive inventory.
- Govern: Focus on governance, risk management, and accountability across your cybersecurity strategy.
- Protect: Implement safeguards, from access control to platform security.
- Detect: Continuously log and monitor your systems for suspicious activity.
- Respond: Develop a plan to manage incidents, contain and mitigate damage.
- Recover: Establish protocols to restore operations swiftly after an incident.
The structure allows you to communicate security needs at different levels within your organization. For instance, at the function level, you might discuss high-level security priorities with your board, while at the subcategory level, you can go into detail with your IT team.
The CSF Tiers
CSF 2.0 offers four implementation tiers: Partial, Risk-Informed, Repeatable, and Adaptive, helping evaluate the maturity of your cybersecurity efforts. Advancing along these tiers demonstrate you strengthen your security posture:
- Partial: Processes are informal, and risk management is limited.
- Risk-Informed: Organizations start prioritizing cybersecurity efforts based on identified risks.
- Repeatable: Security practices are documented and consistently implemented across the organization.
- Adaptive: Organizations anticipate and adapt to changing risks, with an emphasis on continuous improvement.
The CSF Profiles
Profiles are snapshots of your organization’s current cybersecurity practices (Current Profile) and your future goals (Target Profile) allowing companies to document their cybersecurity posture.
Applying the framework
CSF 2.0 is a great framework for organizations at any stage of cybersecurity maturity, offering structured guidance while remaining customizable. The framework is ideal for driving cybersecurity organization-wide at every level: operational for engineers, steering for middle management, and strategic for executive.
To complement this discussion on NIST CSF 2.0, I’d like to introduce my GitHub project: NIST CSF 2.0 Cybersecurity Dashboard. This tool is a free and user-friendly spreadsheet to help small teams or organizations work with the NIST CSF 2.0. It simplifies tracking, prioritizing, and improving cybersecurity measures.
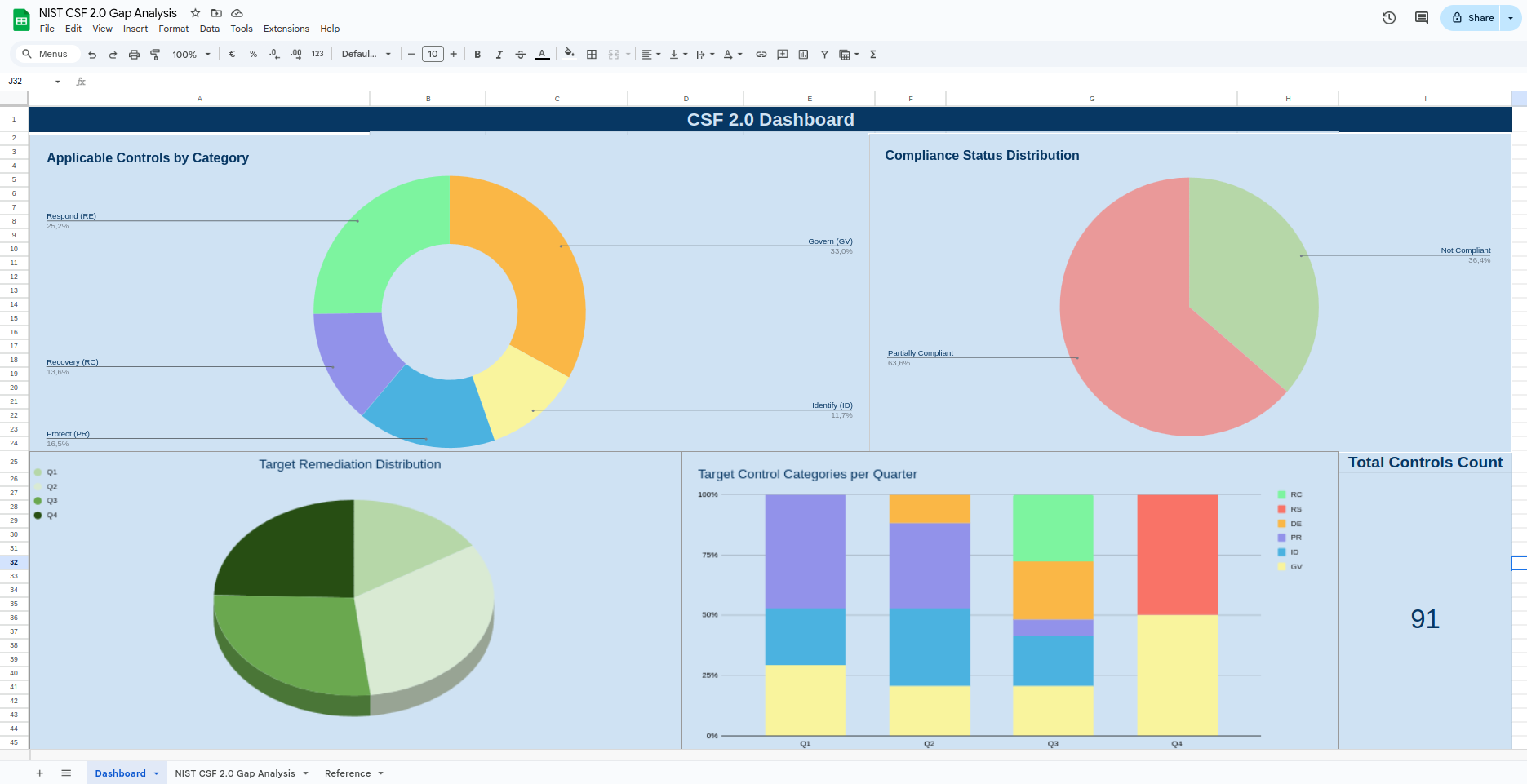
Below are its features:
- Dashboard for Controls by Category: Visualizes the distribution of applicable controls across categories.
- Overall Compliance Status: Shows the percentage of controls that are compliant, partially compliant, and non-compliant.
- Target Remediation Distribution: Displays a distribution of planned remediations over quarters (Q1–Q4 to ensure you can distribute the work over the year and you are not putting too much in your plate with objectives you cannot achieve.
- Target Controls per Quarter: Tracks the number of controls per category slated for completion in each quarter so that you can balance efforts between categories. Remember the overall security level is equal the security of the weakest link, so don't put
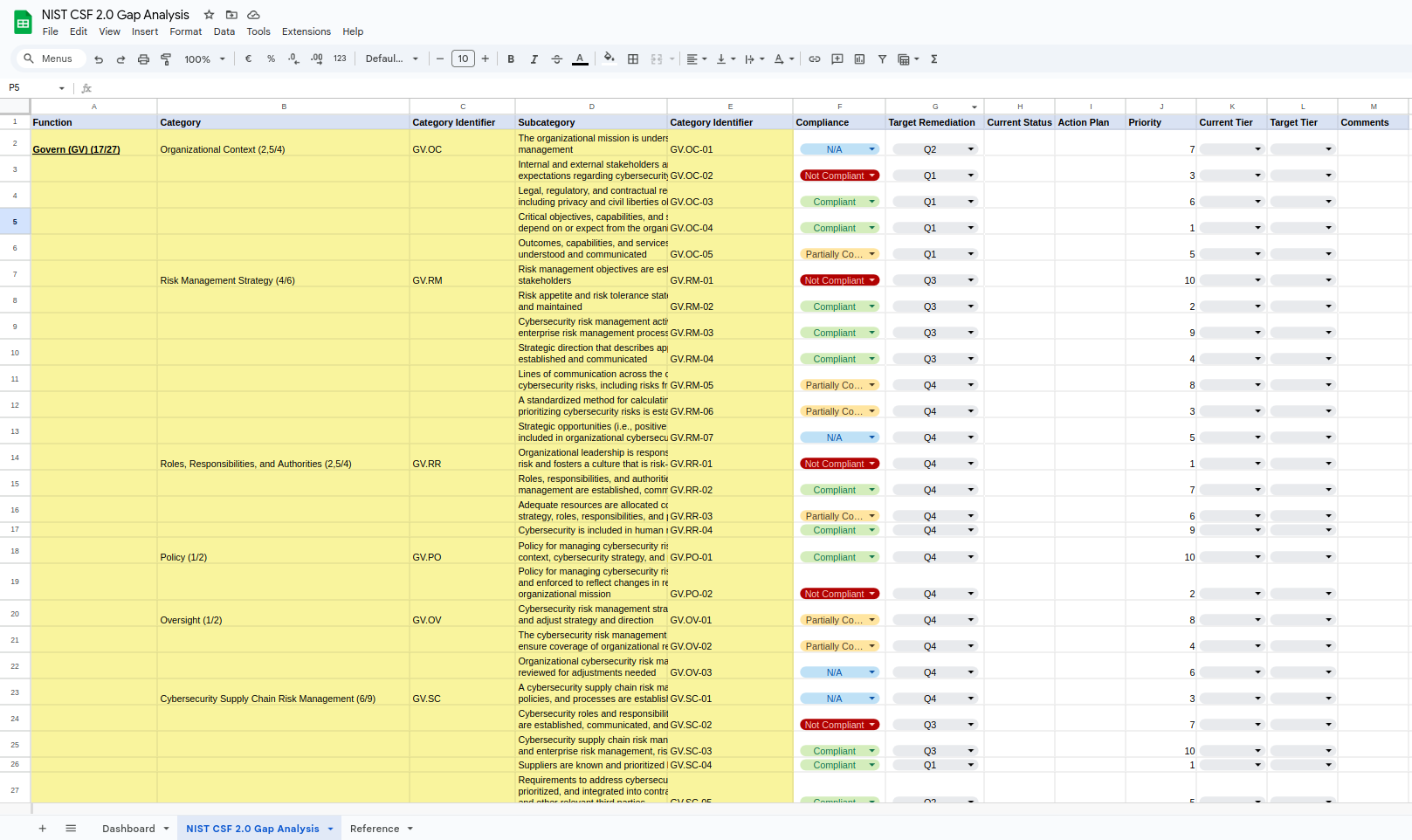
- Control Prioritization: Automatically prioritizes controls based on compliance status, target remediation dates, and other defined criteria to help you address the most critical areas first.
Thank you for reading and do not hesitate to contribute to this project or share feedback with me.
Member discussion