MITRE ATT&CK - Gap Assessment Analysis and Threat Profiling

Introduction: Understanding MITRE ATT&CK Navigator
The MITRE ATT&CK Navigator is a powerful tool that helps cyber security professionals visualize and navigate the extensive ATT&CK matrices. It provides a customizable interface to map out and understand the tactics, techniques, and procedures (TTPs) used by threat actors, making it essential for threat profiling, defensive coverage analysis, and strategic planning. Users can create layers either interactively or programmatically and manipulate cells in the matrix with color coding, adding comments, assigning numerical values to techniques (scoring), etc.
How to Perform a Gap Assessment Using MITRE ATT&CK Navigator
1. Identifying Relevant Threat Groups
Start by identifying the threat groups that are active in your target industry. This can be done by searching through MITRE's CTI groups for threat actors known to target your specific sector.
For example, let's take the aviation industry:
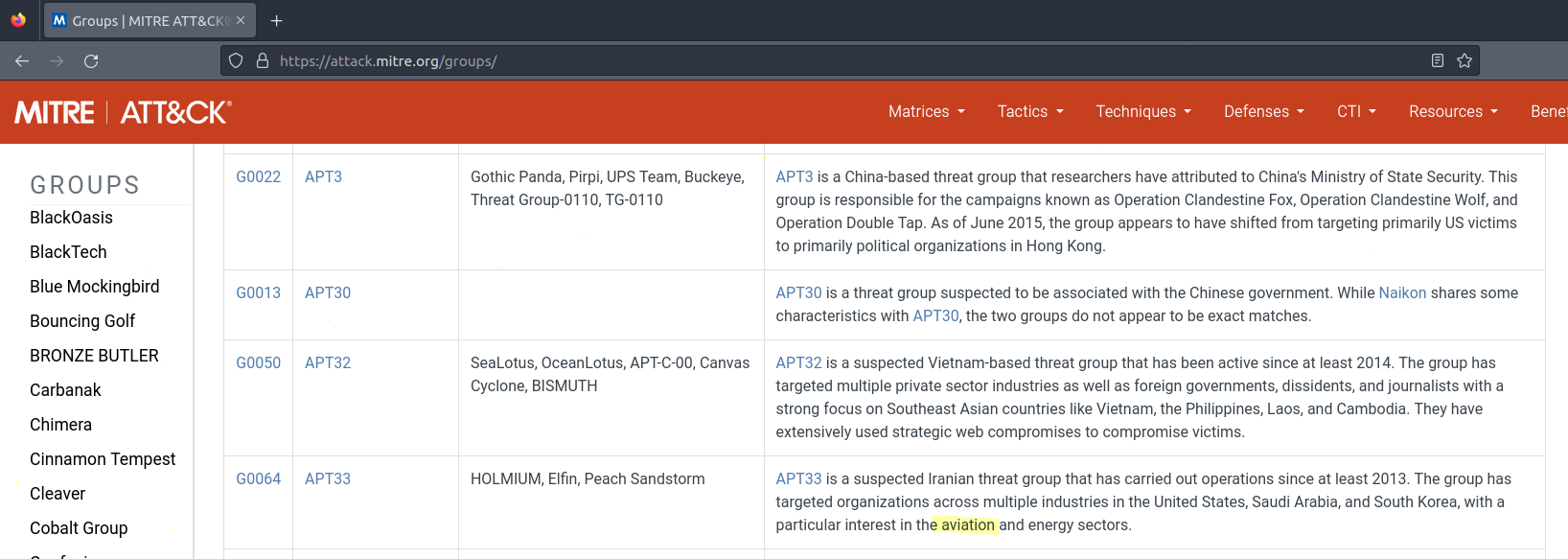
We can enumerate the five following groups:
- G0064 known as APT33: a suspected Iranian threat group that has carried out operations since at least 2013. The group has targeted organizations across multiple industries in the United States, Saudi Arabia, and South Korea, with a particular interest in the aviation and energy sectors.
- G0035 known as Dragonfly: a cyber espionage group that has been attributed to Russia's Federal Security Service (FSB) Center 16. Active since at least 2010, Dragonfly has targeted defense and aviation companies, government entities, companies related to industrial control systems, and critical infrastructure sectors worldwide through supply chain, spearphishing, and drive-by compromise attacks.
- G1001 knowns as HEXANE: a cyber espionage threat group that has targeted oil & gas, telecommunications, aviation, and internet service provider organizations since at least 2017. Targeted companies have been located in the Middle East and Africa, including Israel, Saudi Arabia, Kuwait, Morocco, and Tunisia. HEXANE's TTPs appear similar to APT33 and OilRig but due to differences in victims and tools it is tracked as a separate entity.
- G0065 known as Leviathan: a Chinese state-sponsored cyber espionage group that has been attributed to the Ministry of State Security's (MSS) Hainan State Security Department and an affiliated front company. Active since at least 2009, Leviathan has targeted the following sectors: academia, aerospace/aviation, biomedical, defense industrial base, government, healthcare, manufacturing, maritime, and transportation across the US, Canada, Europe, the Middle East, and Southeast Asia.
- G1018 known as TA2541: a cybercriminal group that has been targeting the aviation, aerospace, transportation, manufacturing, and defense industries since at least 2017. TA2541 campaigns are typically high volume and involve the use of commodity remote access tools obfuscated by crypters and themes related to aviation, transportation, and travel.
Obtain the layer for each of these threat groups:
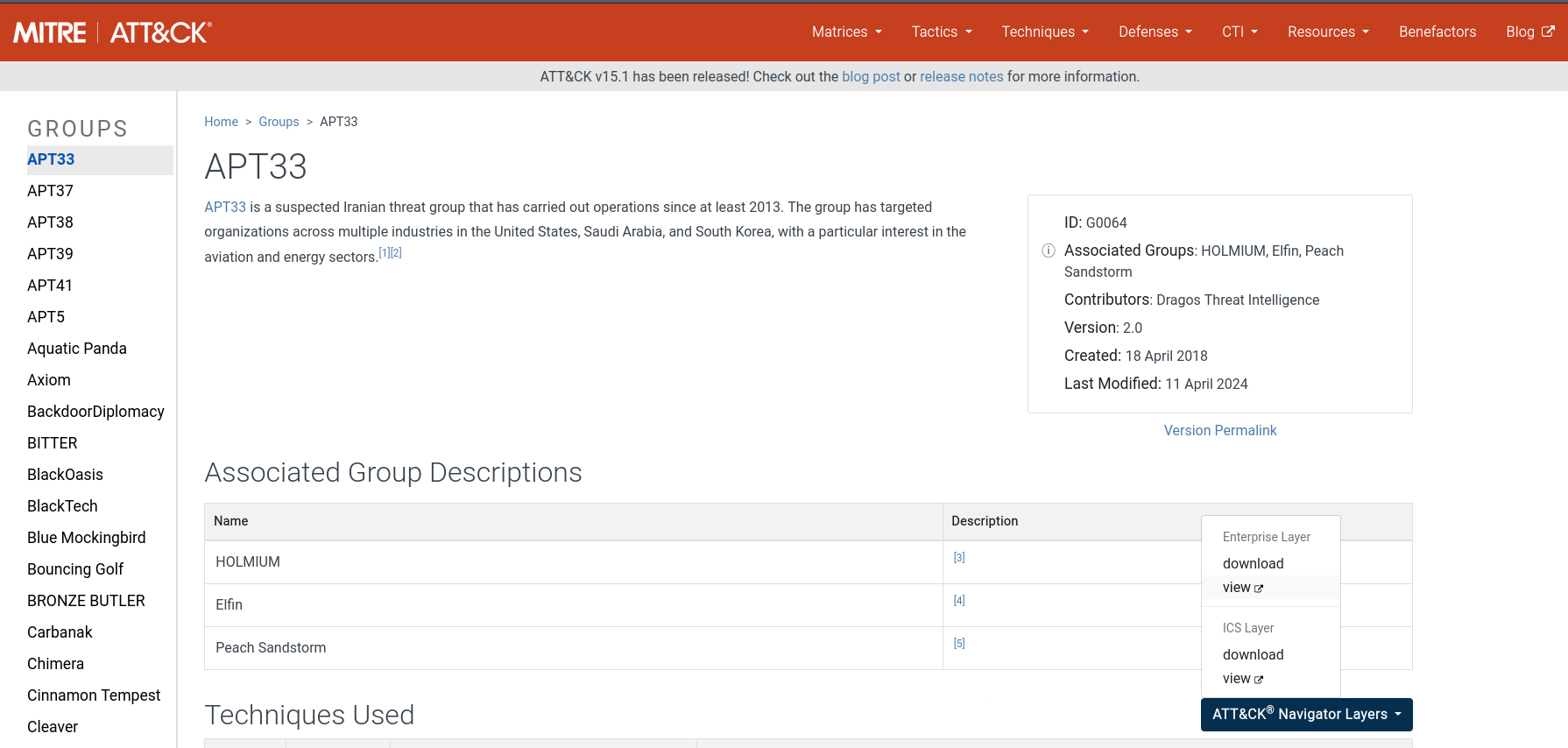
The layer of a threat group highlights its techniques and sub-techniques:
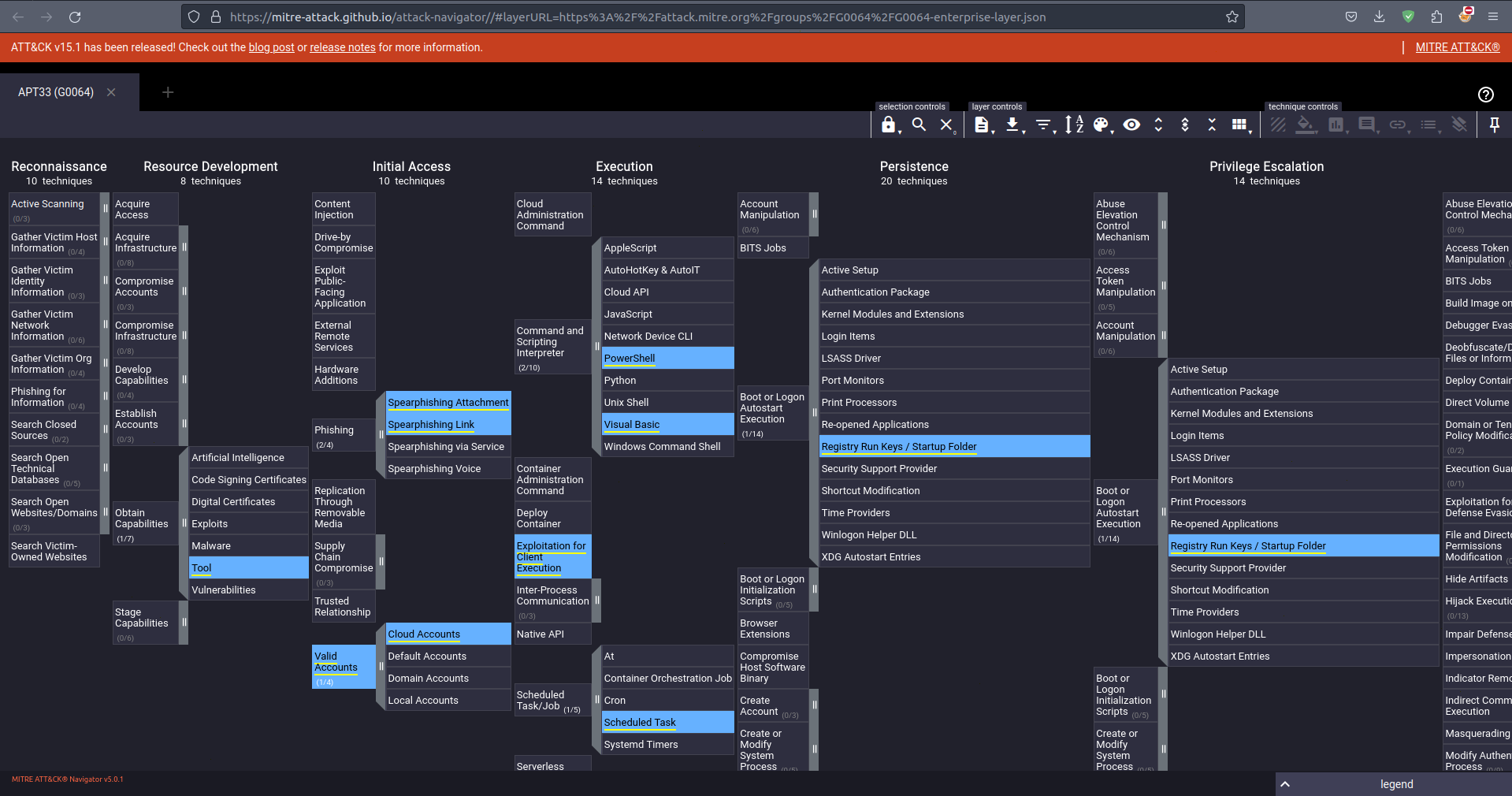
2. Aggregating Threat Group Layers
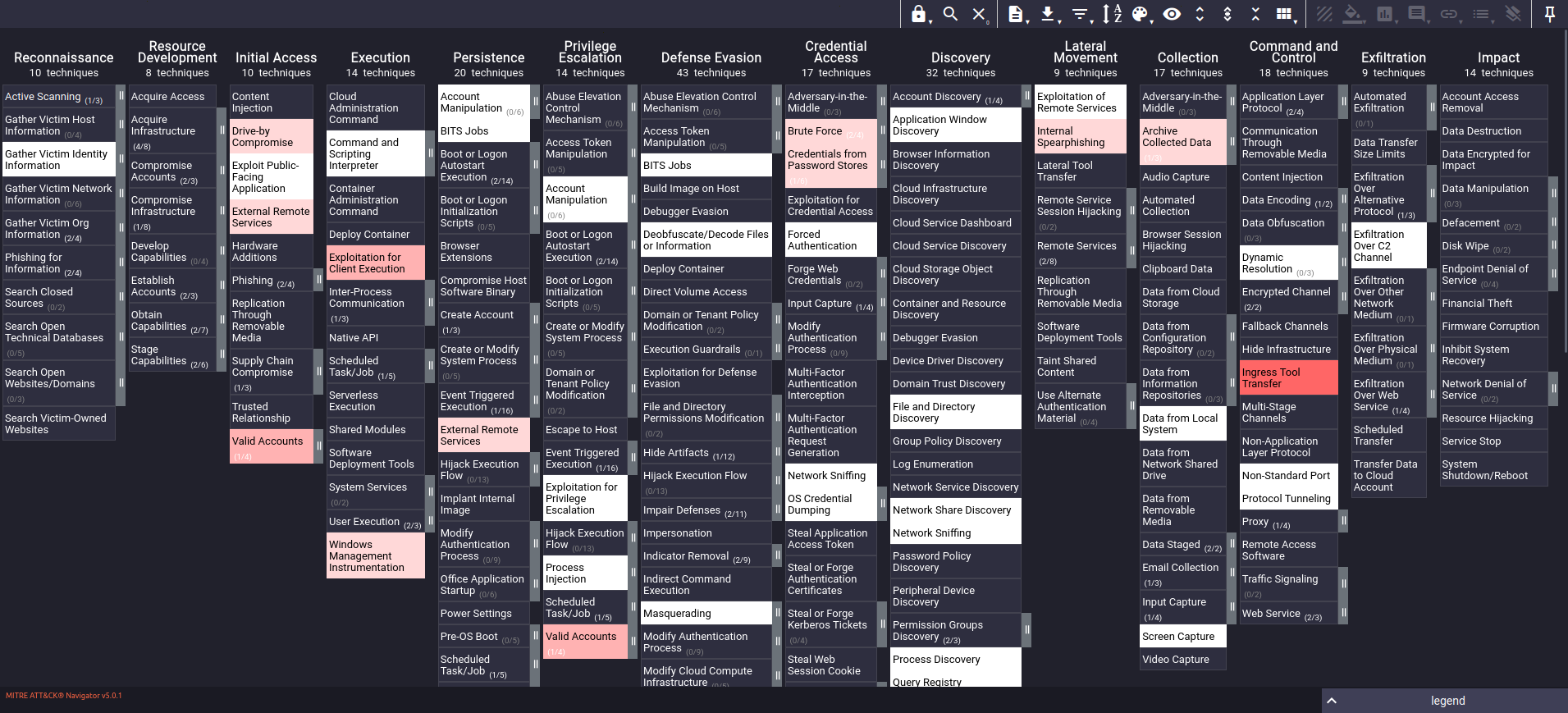
Once you have the individual layers for all relevant threat groups, combine these layers to create a comprehensive threat landscape. In this example, the combined layer will be the simple sum of all the previous individual threat group layers. Eventually you can tweak the score expression adding more weight to certain threat actors you consider more important based on various factors such as their number of recent attacks, the targeted country, the targeted technology stack, etc.
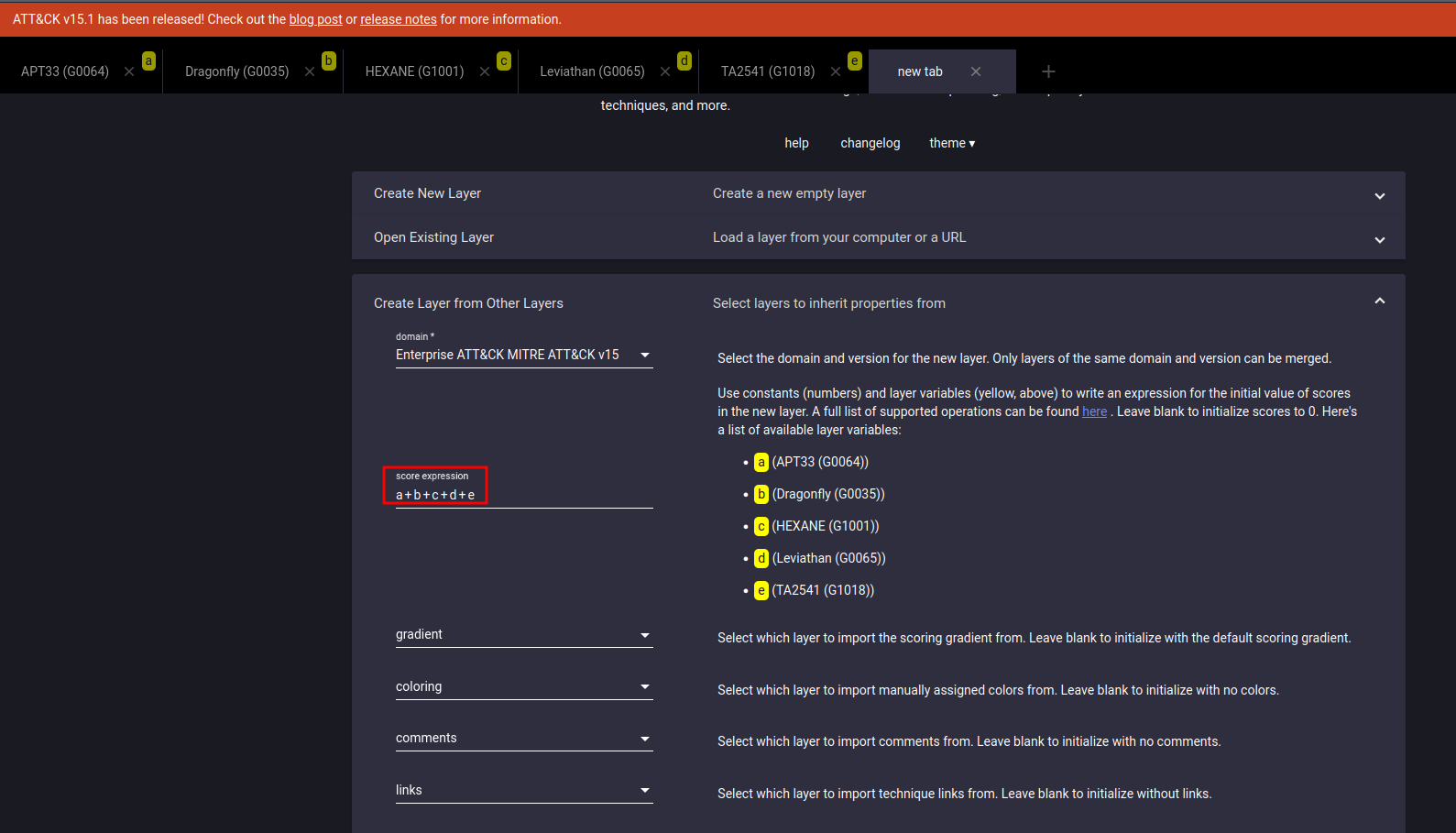
This aggregated view will help in understanding the full scope of potential threats targeting your industry that your organization might face.
3. Mapping Defensive Coverage
Create a layer that outlines your current defensive measures. This layer should include all the controls, technologies, and processes your organization has in place to defend against threats. You can start building your defenses layer based on mitigations that you already implemented.
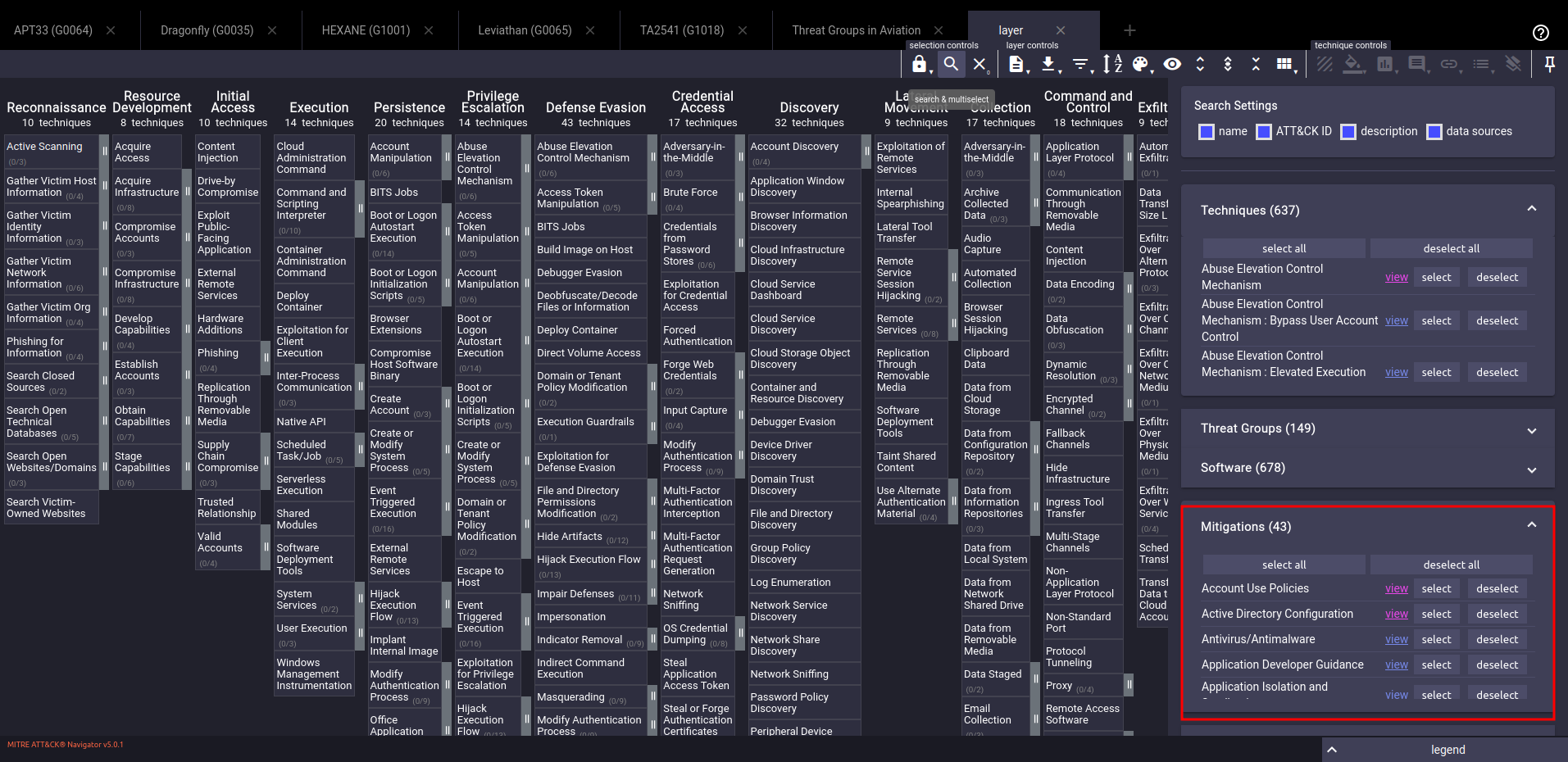
Again, you can adjust the scoring of mitigations you consider more important based on factors such as the perimeter of your infrastructure they cover, the number of solutions you have for the same mitigation (defense in depth), their effectiveness based on reporting, etc.
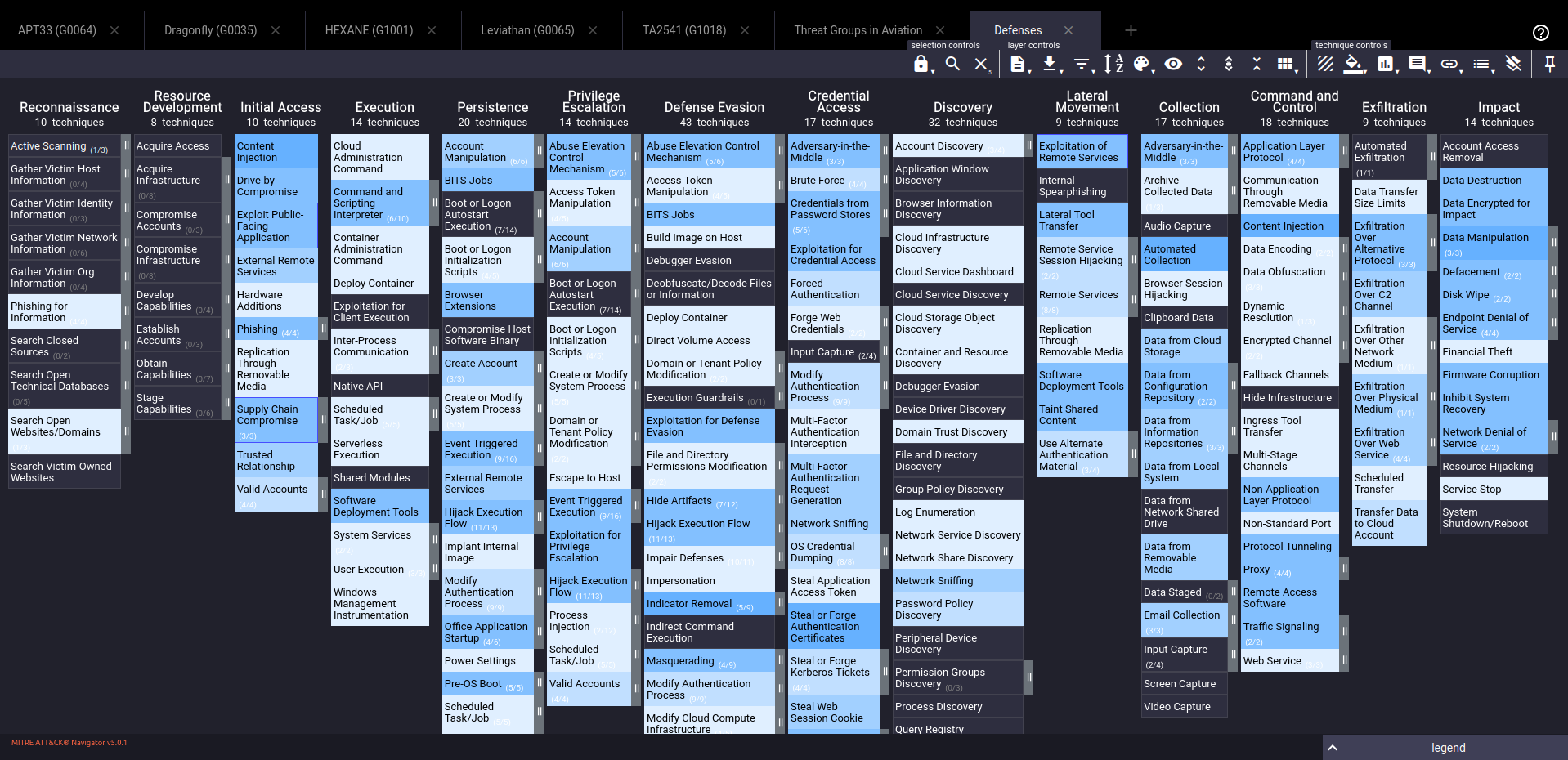
4. Identifying Gaps
Subtract your defensive coverage layer from the combined threat groups layer. The result will highlight the gaps in your defense where threat actors have techniques that are not adequately mitigated by your current security measures.
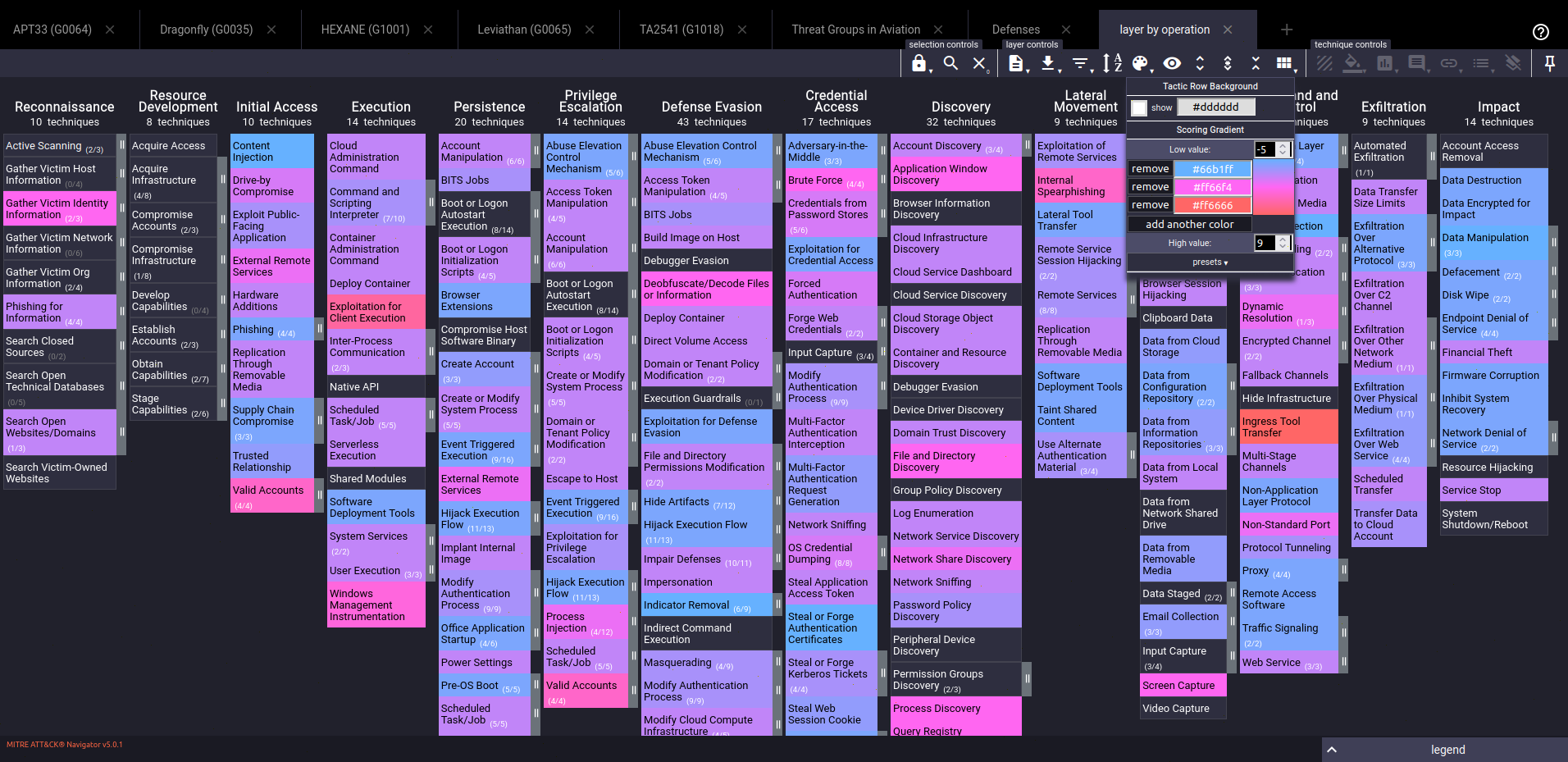
The scoring gradient ranges from blue (lowest) to red (highest). Blue cells indicate areas where no techniques are used by threat actors but mitigations have been implemented. Conversely, red or magenta cells indicate critical gaps where threat actor techniques pierce your defenses due to the absence of mitigations.
Building and Prioritizing Mitigation Layers
1. Building Mitigation Layers
Based on the identified threat actors or gaps, create a layer that outlines potential mitigations. These mitigations should address the uncovered techniques and be tailored to your organization's specific needs and capabilities.
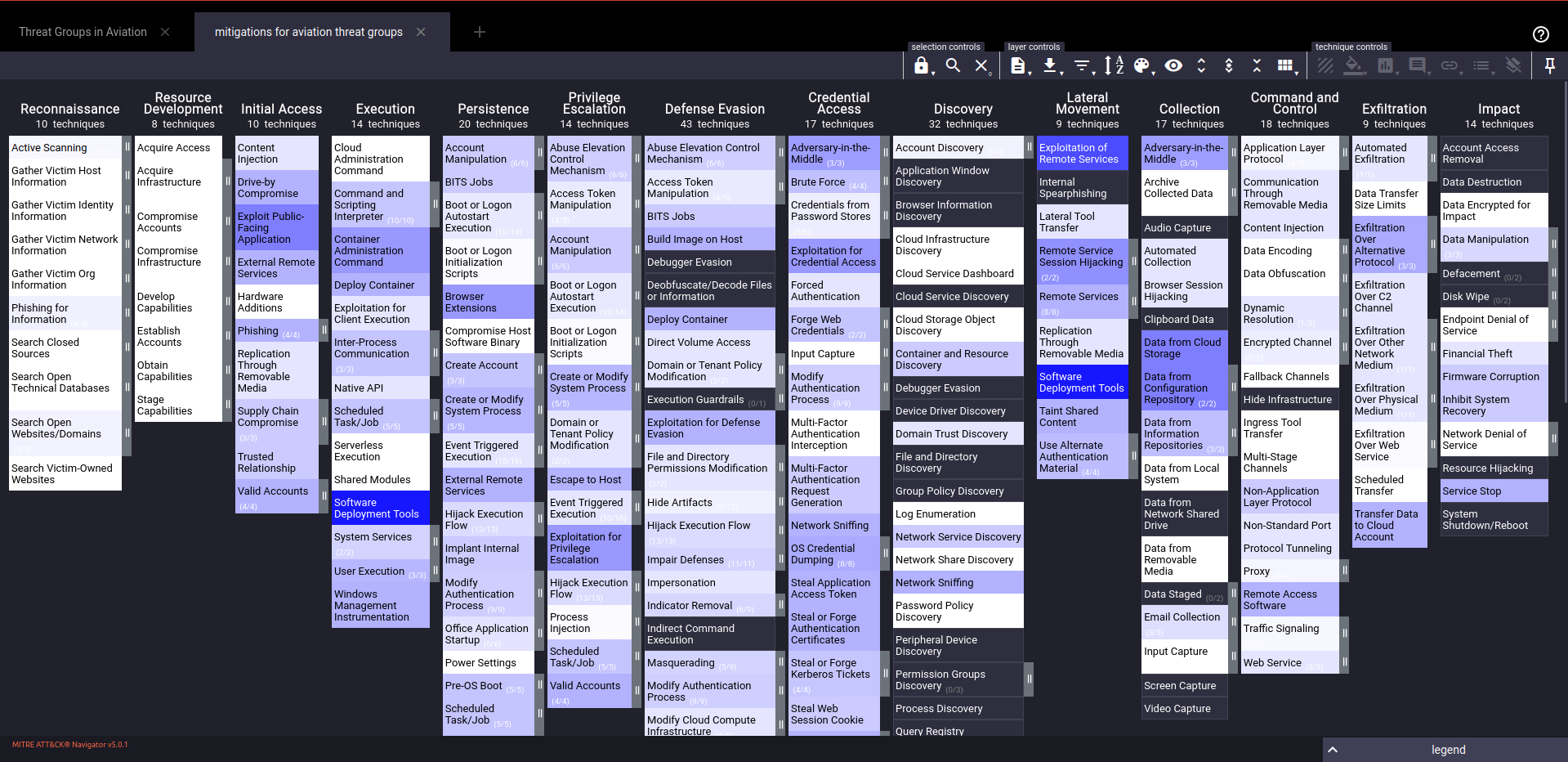
2. Prioritizing Mitigations
Prioritize mitigations based on their frequency of occurrence and their impact score. This will help in focusing resources on the most critical areas, ensuring efficient and effective risk management.
For example, in the aviation sector:
We have these 3 mitigations that are top-priority to cover most of the techniques used by threat groups targeting the aviation industry:
- M1031 (Network Intrusion Prevention): Use intrusion detection signatures to block traffic at network boundaries.
- M1026 (Privileged Account Management): Manage the creation, modification, use, and permissions associated to privileged accounts, including SYSTEM and root.
- M1018 (User Account Management): Manage the creation, modification, use, and permissions associated to user accounts.
Presenting Threat Profiler: an Automated Threat Profiling Tool that Helps Building Mitigations
To streamline the threat profiling and mitigation analysis process, I've developed a tool named Threat Profiler. This tool automates the following:
Searching for threat actors by keyword (e.g., sector).
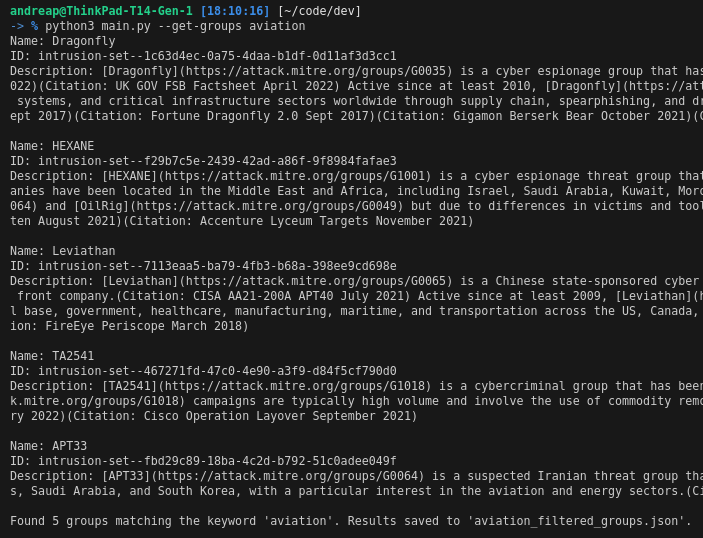
Downloading threat group layers.
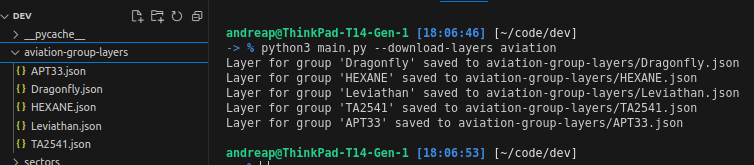
Combining these layers to form a comprehensive threat landscape.
Building a mitigations layer based on the techniques used by identified threat actors in the combined layers.
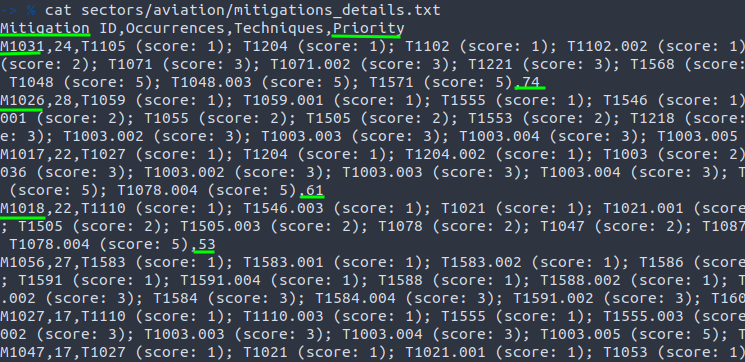
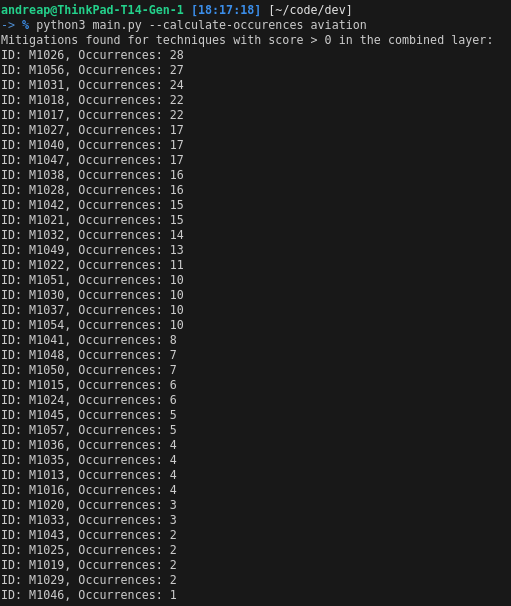
Prioritizing these mitigations to ensure the most critical areas are addressed first. The priority of each mitigation is calculated as follows:
Priority of a Mitigation MI = (Number of occurrences of mitigation MI among techniques present in the combined threats layer) × (Weight of the techniques mitigated by MI).
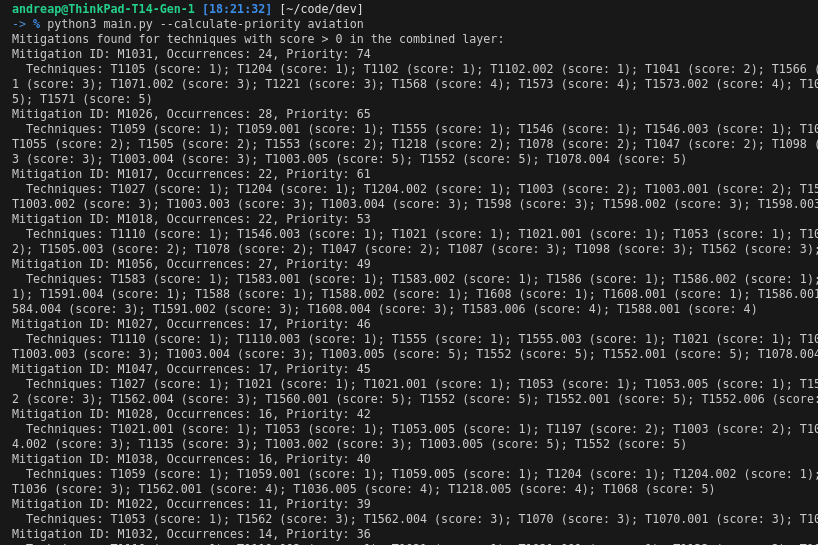
This calculation considers both the frequency with which a mitigation is applied across different techniques and the importance (weight) of the techniques it mitigates. This ensures that more frequently occurring and higher-impact mitigations are prioritized, focusing resources on the most significant vulnerabilities.
More Resources
1. ETDA's Threat Actor Encyclopedia
ETDA's Threat Actor Encyclopedia is an online threat intelligence database providing detailed profiles of threat groups worldwide as "cards" and their TTPs. Initially published as a PDF in 2019 under ThaiCERT, the portal compiles information from public sources (OSINT) and contributions from antivirus and security organizations. The portal also offers data in MISP galaxy/cluster format for easy integration into existing systems.
Sources Used:
- MISP Threat Actors Galaxy
- MITRE ATT&CK Framework
- Malpedia
- AlienVault Open Threat Exchange (OTX)
Here are some examples of how the ETDA Threat Actor Encyclopedia can be used in practice:
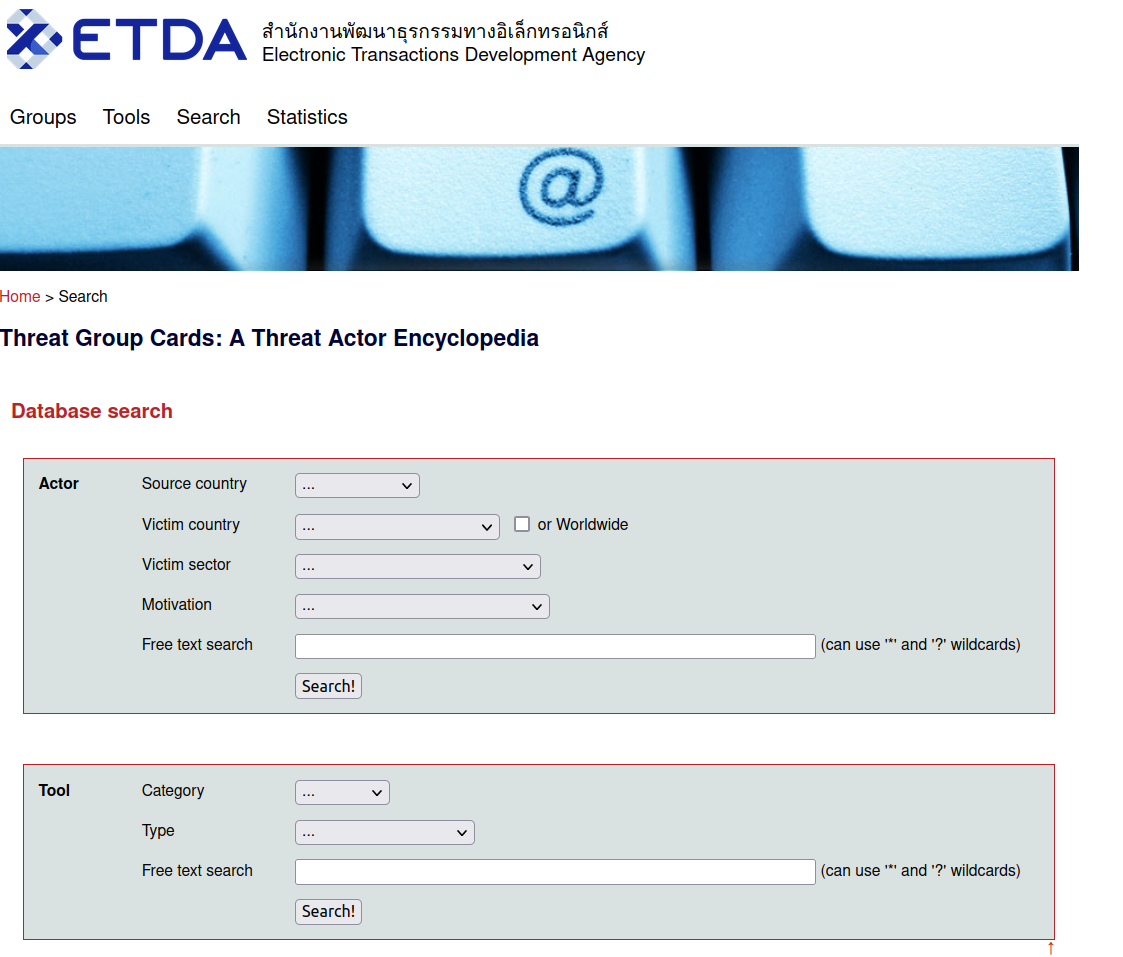
- Database Search Tool: This interface allows users to quickly search for threat actors based on source country of attacks, victim country, victim sector, motivation and keywords.
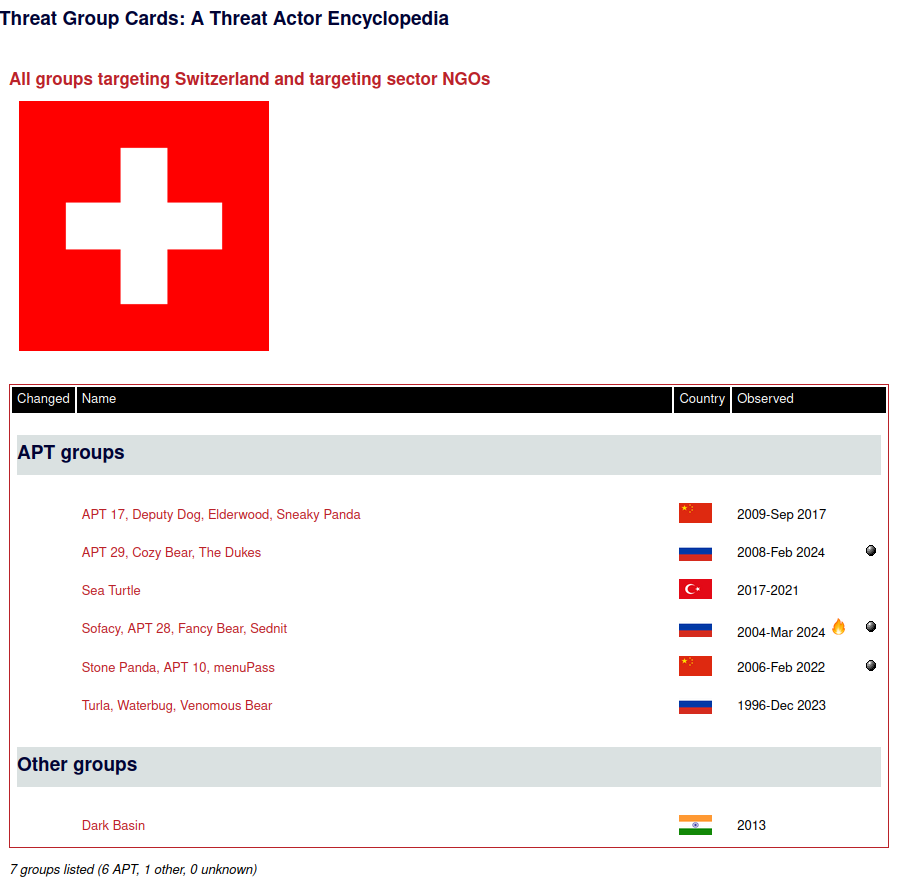
- Search Example for NGOs in Switzerland: This search provides a detailed threat profile for targeted NGOs in Switzerland.
2. Control Validation Compass
Control Validation Compass is an open-source tool developed by Scott Small to aid in threat modeling and security control validation.
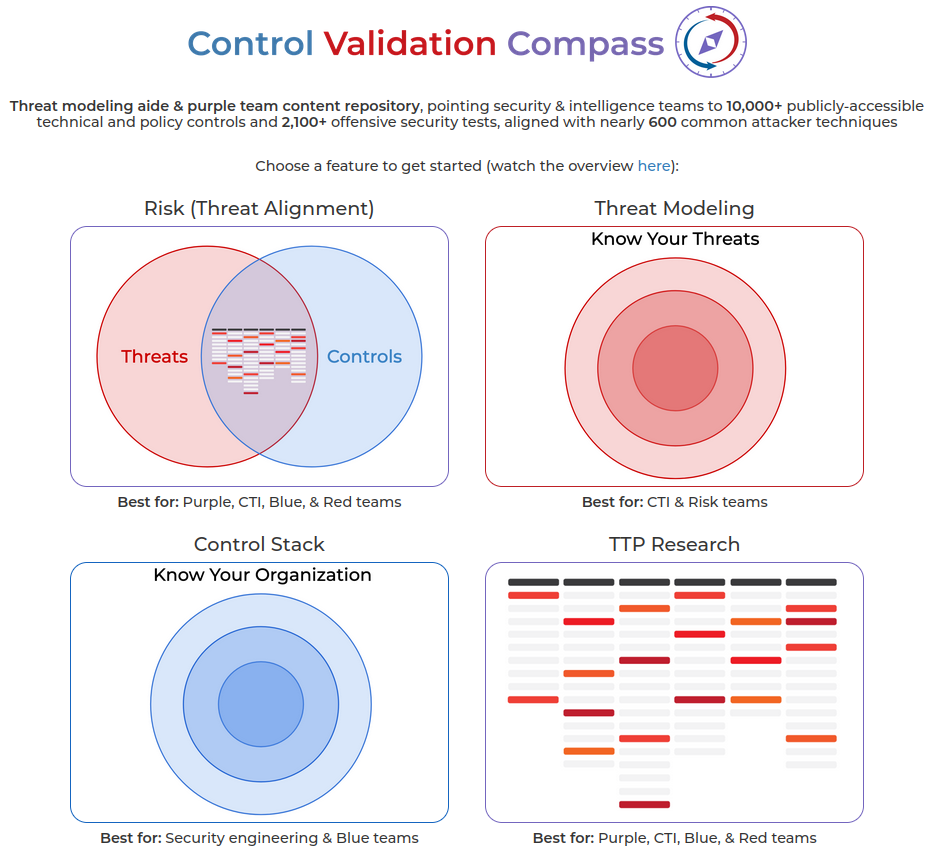
Here’s its four features:
- Threat Modeling: Build a MITRE ATT&CK layer to identify threats based on victim industry, location, and adversary motivation.
- Controls Lookup: Find attacker technique-mapped detections and tests across your security stack.
- Threat Alignment: Combine threat modeling and controls lookup to align your security controls and policies with the identified threat profile.
- TTP Research: Research specfic adversary techniques to find corresponding policy controls, detection rules, and offensive tests to validate controls.
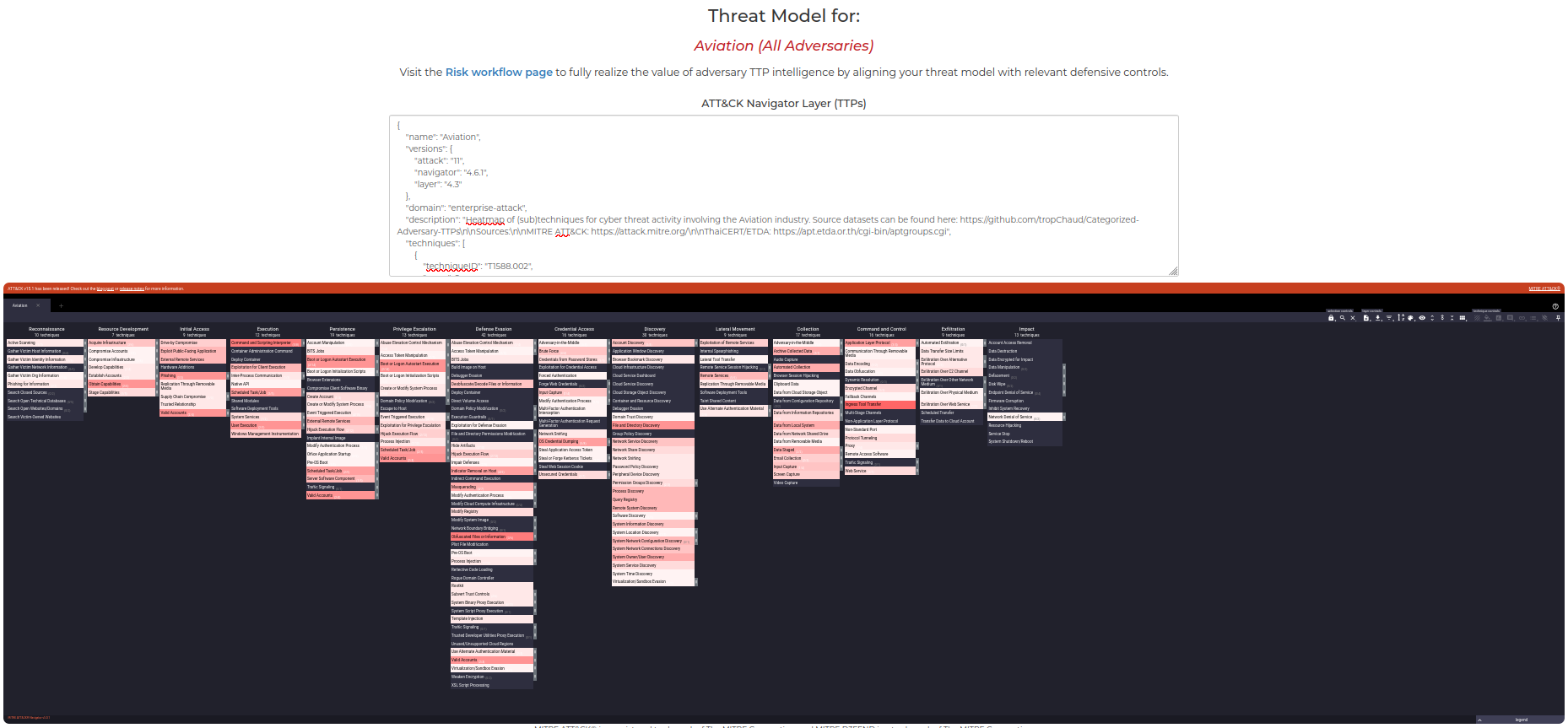
Using the Threat Modeling feature, you can build a MITRE ATT&CK layer that identifies threats based on your specific context, such as industry or location.
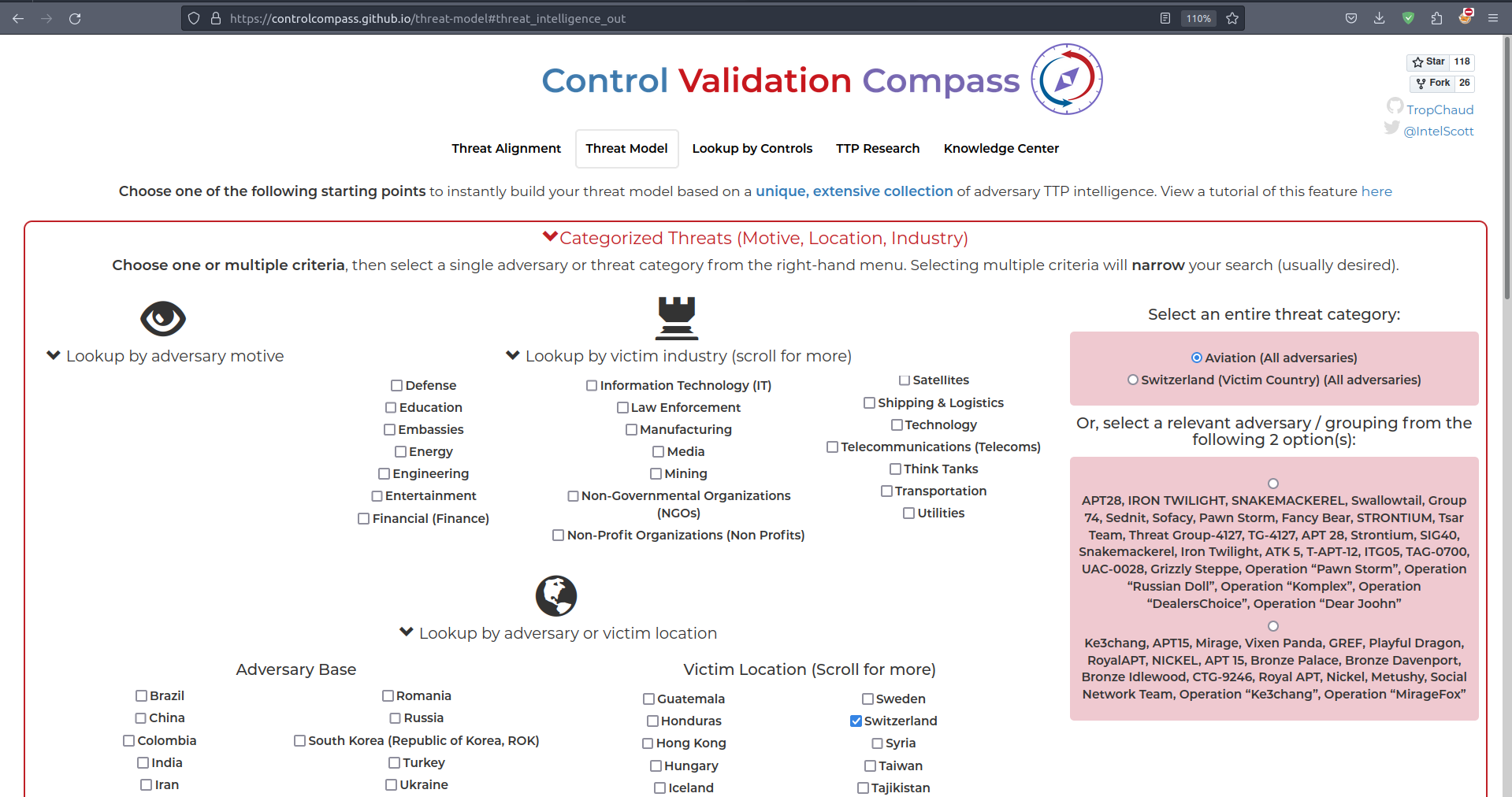
This screenshot shows a threat model specifically created for the aviation industry, highlighting the relevant TTPs:
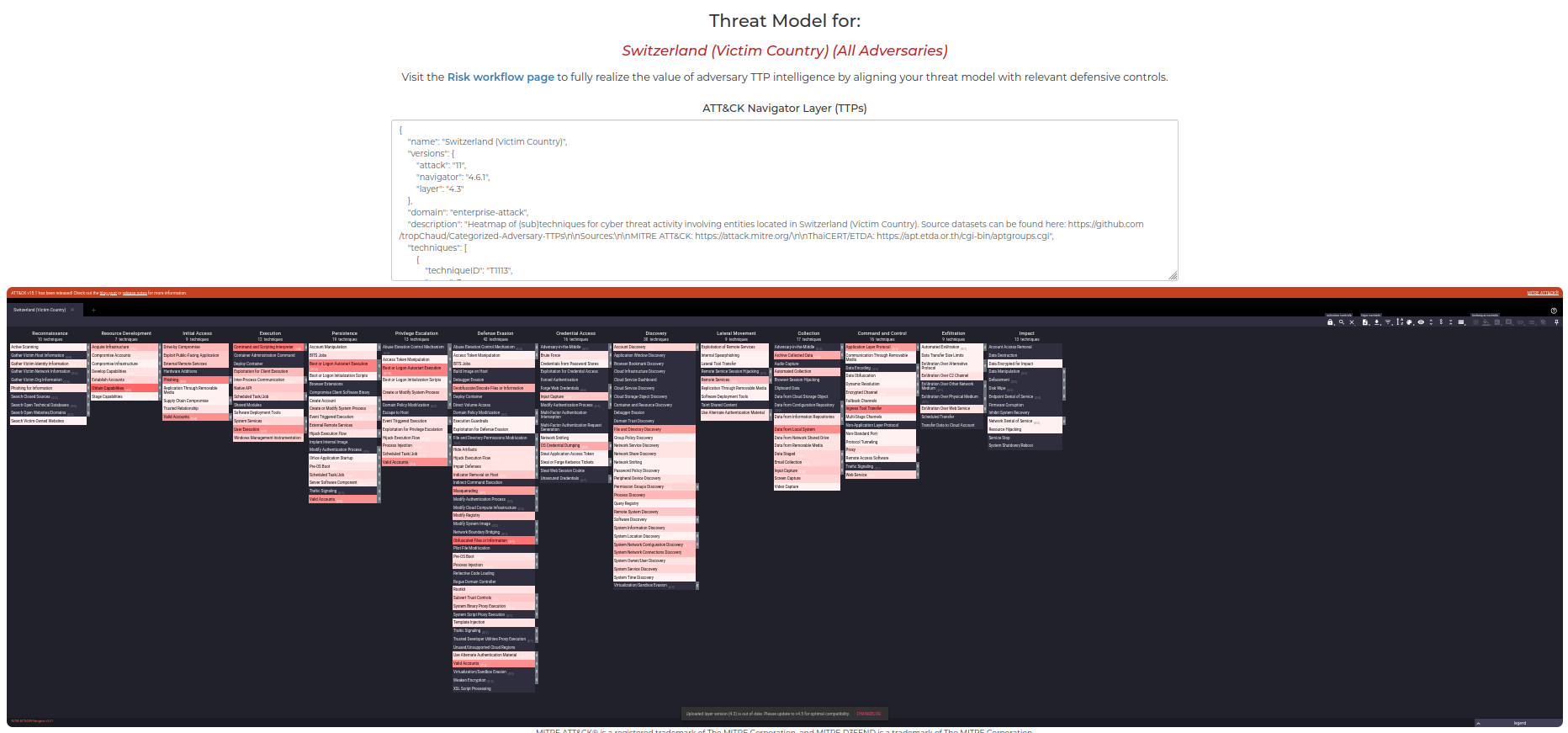
Here, we have a threat model focused on Switzerland:
Conclusion
While threat intelligence typically requires a certain level of cybersecurity maturity within an organization—such as having a robust security infrastructure, incident response plans, and dedicated security personnel—starting with threat modeling is accessible and beneficial for all. It allows you to navigate the threat landscape with a rudder and not blindly. Threat modeling helps you understand what threats you need to be prepared for and prioritize necessary mitigations. The tools I've showcased make it easy to build a tailored threat model for your organization, automate the process, and regularly update it to stay informed.