SIEM - Guide to Windows Event Logs Auditing and Forwarding

Introduction
Collecting Windows Event logs is crucial for maintaining a secure and well-monitored IT environment. Whether it’s tracking user logins, monitoring changes to critical systems, or detecting potential security threats, Windows event logs provide the detailed visibility you need to understand what's happening across your network—especially on critical machines like Domain Controllers (DCs). Without these logs, you’re basically flying blind when it comes to identifying issues or investigating incidents.
In this guide, I'll walk you through how to properly set up Windows event logging so you can capture and forward these logs to your SIEM, it can be Splunk, ELK, or any other platform of your choice. The goal is to centralize your event data.
To get there, we’ll start by configuring Group Policy Objects (GPOs) on your Windows machines (domain controllers, servers, and workstations) to ensure they’re collecting the right types of events, such as login attempts, policy changes, and security logs. Then, we’ll set up the Windows Event Collector (WEC) server, which will act as a central hub, receiving logs from all your Windows machines configured as Event Forwarders.
Finally, I’ll show you how to configure custom channels and subscriptions on the WEC server to organize and filter the events before forwarding them to your SIEM for analysis. By the end of this guide, you’ll have a streamlined setup that ensures critical logs are always captured and available for monitoring in your SIEM.
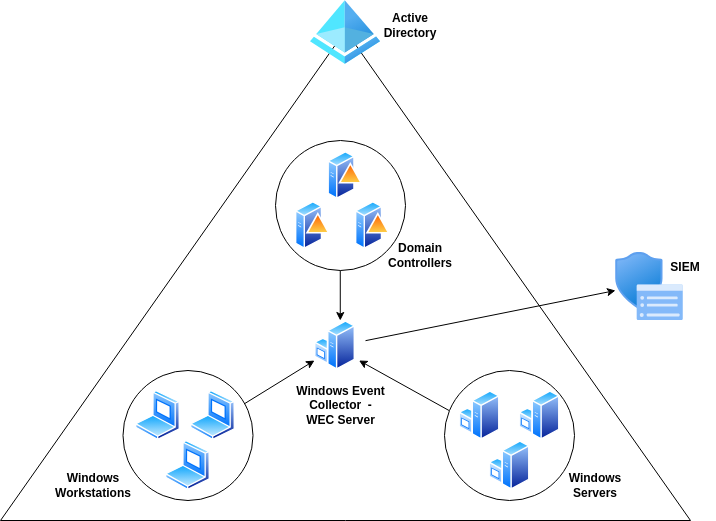
Table of Contents
- Introduction
- Prerequisites
- GPO Configuration for Member Servers
- GPO Configuration for Domain Controllers (DCs)
- GPO Configuration for Workstations
- GPO for Event Collector
- GPO for Event Forwarders
- GPO for WinRM Security Hardening
- Configuring Subscriptions on the WEC Server
- Useful Resources
GPO Configuration for Member Servers
Step 1: Create the GPO
- Open Group Policy Management Console:
- Press
Win + R, typegpmc.msc, and press Enter.
- Press
- Navigate to Your Domain:
- Expand your forest, then your domain.
- Locate the Servers OU:
- Find the OU containing your Member Servers.
- Create a New GPO:
- Right-click the Group Policy Objects or the Servers OU and select Create a GPO in this domain, you can link it later or link it directly to the Servers OU....
Name the GPO: GPO_Member_Servers_Security_Audit.
Step 2: Configure the GPO Settings
- Edit the GPO:
- Right-click the newly created GPO and select Edit.
- Navigate to Advanced Audit Policy Configuration:
- Go to:
Computer Configuration → Policies → Windows Settings → Security Settings → Advanced Audit Policy Configuration → Audit Policies
- Go to:
Configure Audit Policies:
Expand each audit category and configure the policies as per the table below.
Audit Policies and Settings for Member Servers
| Audit Category | Policy Name | Base Recommendation | Stronger Recommendation | Events IDs Monitored |
|---|---|---|---|---|
| Account Logon | Credential Validation | Success | Success and Failure | 4774-4777 |
| Kerberos Authentication Service | Success and Failure | 4768, 4771, 4772, 4820 | ||
| Kerberos Service Ticket Operations | Success and Failure | 4769, 4770, 4773 | ||
| Other Account Logon Events | Success and Failure | |||
| Account Management | Computer Account Management | Success | Success and Failure | 4741-4743 |
| Other Account Management Events | Success and Failure | Success and Failure | 4739, 4782, 4793 | |
| Security Group Management | Success and Failure | Success and Failure | 4727-4737, 4754-4758, 4764, 4799 | |
| User Account Management | Success and Failure | Success and Failure | 4720, 4722-4726, 4738, 4740, 4765-4767, 4780, 4781, 4794, 5376, 5377 | |
| Detailed Tracking | DPAPI Activity | Success and Failure | 4692-4695 | |
| Process Creation | Success | Success and Failure | 4688, 4696 | |
| Logon/Logoff | Account Lockout | Success | ||
| IPsec Main Mode | IF and IF | 4646, 4650-4655, 4976, 4979, 4980-4984, 5453 | ||
| Logoff | Success | Success | 4634, 4647 | |
| Logon | Success and Failure | Success and Failure | 4624-4626, 4648, 4675 | |
| Special Logon | Success | Success and Failure | 4672, 4964 | |
| Policy Change | Audit Policy Change | Success and Failure | Success and Failure | 4715, 4719, 4817, 4902, 4904-4908, 4912 |
| Authentication Policy Change | Success | Success and Failure | 4706, 4707, 4713, 4716-4718, 4865-4867 | |
| MPSSVC Rule-Level Policy Change | Success | 4944-4952, 4954, 4956-4958 | ||
| System | IPsec Driver | Success and Failure | Success and Failure | 5478, 5479, 5480, 5483-5485 |
| Security State Change | Success and Failure | Success and Failure | 4608, 4609, 4616, 4621 | |
| Security System Extension | Success and Failure | Success and Failure | 4610, 4611, 4614, 4622, 4697 | |
| System Integrity | Success and Failure | Success and Failure | 4612, 4615, 4618, 5038, 5056, 5061, 5890, 6281, 6410 |
¹ Note: To audit command-line processes for event 4688, enable the following policy:
- Navigate to:
Computer Configuration → Policies → Administrative Templates → System → Audit Process Creation - Enable Include command line in process creation events.
Enabling command-line auditing may generate a large volume of logs. Ensure that your event log sizes are appropriately configured to handle this data without overwriting important events.
Step 3: Enforce the Audit Policy Settings
- Ensure that the following setting is enabled to enforce the advanced audit policy configurations:
- Navigate to:
Computer Configuration → Policies → Windows Settings → Security Settings → Local Policies → Security Options - Set Audit: Force audit policy subcategory settings (Windows Vista or later) to override audit policy category settings to Enabled.
- Navigate to:
GPO Configuration for Domain Controllers (DCs)
Name : GPO_Domain_Controllers_Security_Audit
Repeat the same steps used for the previous GPO with the following Windows Events IDs table :
Audit Policies and Settings for Domain Controllers
| Audit Category | Policy Name | Base Recommendation | Stronger Recommendation | Events IDs Monitored |
|---|---|---|---|---|
| Account Logon | Credential Validation | Success | Success and Failure | 4774-4777 |
| Kerberos Authentication Service | Success and Failure | 4768, 4771, 4772, 4820 | ||
| Kerberos Service Ticket Operations | Success and Failure | 4769, 4770, 4773 | ||
| Other Account Logon Events | Success and Failure | |||
| Account Management | Computer Account Management | Success and Failure | Success and Failure | 4741-4743 |
| Other Account Management Events | Success and Failure | Success and Failure | 4739, 4782, 4793 | |
| Security Group Management | Success and Failure | Success and Failure | 4727-4737, 4754-4758, 4764, 4799 | |
| User Account Management | Success and Failure | Success and Failure | 4720, 4722-4726, 4738, 4740, 4765-4767, 4780, 4781, 4794, 5376, 5377 | |
| Detailed Tracking | DPAPI Activity | Success and Failure | 4692-4695 | |
| Process Creation | Success | Success and Failure | 4688, 4696 | |
| DS Access | Directory Service Access | Success and Failure | Success and Failure | 4661, 4662 |
| Directory Service Changes | Success and Failure | Success and Failure | 5136-5139, 5141, 5169, 5170 | |
| Logon/Logoff | Account Lockout | Success | ||
| IPsec Main Mode | IF and IF | 4646, 4650-4655, 4976, 4979, 4980-4984, 5453 | ||
| Logoff | Success | Success | 4634, 4647 | |
| Logon | Success and Failure | Success and Failure | 4624-4626, 4648, 4675 | |
| Special Logon | Success | Success and Failure | 4672, 4964 | |
| Policy Change | Audit Policy Change | Success and Failure | Success and Failure | 4715, 4719, 4817, 4902, 4904-4908, 4912 |
| Authentication Policy Change | Success | Success and Failure | 4706, 4707, 4713, 4716-4718, 4865-4867 | |
| MPSSVC Rule-Level Policy Change | Success | 4944-4952, 4954, 4956-4958 | ||
| System | IPsec Driver | Success and Failure | Success and Failure | 5478, 5479, 5480, 5483-5485 |
| Security State Change | Success and Failure | Success and Failure | 4608, 4609, 4616, 4621 | |
| Security System Extension | Success and Failure | Success and Failure | 4610, 4611, 4614, 4622, 4697 | |
| System Integrity | Success and Failure | Success and Failure | 4612, 4615, 4618, 5038, 5056, 5061, 5890, 6281, 6410 |
GPO Configuration for Workstations
Name : GPO_Workstations_Security_Audit
Repeat the same steps used for the previous GPO with the following Windows Events IDs table :
Audit Policies and Settings for Workstations
| Audit Category | Policy Name | Base Recommendation | Stronger Recommendation | Events IDs Monitored |
|---|---|---|---|---|
| Account Logon | Credential Validation | Success | Success and Failure | 4774-4777 |
| Kerberos Authentication Service | Success and Failure | 4768, 4771, 4772, 4820 | ||
| Kerberos Service Ticket Operations | Success and Failure | 4769, 4770, 4773 | ||
| Other Account Logon Events | Success and Failure | |||
| Account Management | Computer Account Management | Success | Success and Failure | 4741-4743 |
| Other Account Management Events | Success | Success and Failure | 4739, 4782, 4793 | |
| Security Group Management | Success | Success and Failure | 4727-4737, 4754-4758, 4764, 4799 | |
| User Account Management | Success | Success and Failure | 4720, 4722-4726, 4738, 4740, 4765-4767, 4780, 4781, 4794, 5376, 5377 | |
| Detailed Tracking | DPAPI Activity | Success and Failure | 4692-4695 | |
| Process Creation | Success | Success and Failure | 4688, 4696 | |
| Logon/Logoff | Account Lockout | Success | ||
| IPsec Main Mode | IF and IF | 4646, 4650-4655, 4976, 4979, 4980-4984, 5453 | ||
| Logoff | Success | Success | 4634, 4647 | |
| Logon | Success and Failure | Success and Failure | 4624-4626, 4648, 4675 | |
| Special Logon | Success | Success and Failure | 4672, 4964 | |
| Policy Change | Audit Policy Change | Success and Failure | Success and Failure | 4715, 4719, 4817, 4902, 4904-4908, 4912 |
| Authentication Policy Change | Success | Success and Failure | 4706, 4707, 4713, 4716-4718, 4865-4867 | |
| MPSSVC Rule-Level Policy Change | Success | 4944-4952, 4954, 4956-4958 | ||
| System | IPsec Driver | Success and Failure | Success and Failure | 5478, 5479, 5480, 5483-5485 |
| Security State Change | Success and Failure | Success and Failure | 4608, 4609, 4616, 4621 | |
| Security System Extension | Success and Failure | Success and Failure | 4610, 4611, 4614, 4622, 4697 | |
| System Integrity | Success and Failure | Success and Failure | 4612, 4615, 4618, 5038, 5056, 5061, 5890, 6281, 6410 |
GPO for Event Collectors
- Name:
GPO_EventCollector_Configuration - Purpose: Configures the Windows Event Collector (WEC) servers, enabling them to receive and manage event logs.
Steps to Create:
- Open the Group Policy Management Console (GPMC).
- Right-click on the GPO OU or the OU where your Event Collector servers reside, and select Create a GPO in this domain, and link it...
- Name the GPO:
GPO_EventCollector_Configuration. - Right-click the newly created GPO and choose Edit.
Configuration:
- Navigate to:
Computer Configuration -> Policies -> Windows Settings -> Security Settings -> Windows Firewall -> Inbound Rules.- Add a new rule with the following:
- Predefined: Windows Remote Management (HTTP-In).
- Uncheck Public profile.
- Add a new rule with the following:
- Navigate to:
Computer Configuration -> Preferences -> Control Panel Settings -> Services.- Create a new service with:
- Service Name:
Wecsvc. - Action: Start Service.
- Startup Type: Automatic (Delayed Start).
- Service Name:
- Create a new service with:
GPO for Event Forwarders (Member Servers, Domain Controllers and Workstations)
- Name:
GPO_EventForwarder_Configuration - Purpose: Configures the workstations and servers to forward event logs to the Event Collector.
Steps to Create:
- In the GPMC, right-click the GPO OU or the OU containing your workstations and servers, and select Create a GPO in this domain, and link it...
- Name the GPO:
GPO_EventForwarder_Configuration. - Right-click the new GPO and select Edit.
Configuration:
- Navigate to:
Local Policies > User Right Management > Manage auditing and security log.- Select Properties, on the Local Security Setting tab, click Add User or Group to add the Network Service account.
- Navigate to:
Computer Configuration -> Policies -> Administrative Templates -> Windows Components -> Windows Remote Management (WinRM) -> WinRM Service.- Enable Allow remote server management through WinRM and set
*for IPv4.
- Enable Allow remote server management through WinRM and set
- Navigate to:
Computer Configuration -> Preferences -> Control Panel Settings -> Services.- Create a new service with:
- Service Name:
WinRM. - Action: Start Service.
- Startup Type: Automatic (Delayed Start).
- Service Name:
- Create a new service with:
- Navigate to:
Computer Configuration -> Policies -> Windows Settings -> Security Settings -> Windows Firewall -> Inbound Rules.- Add a new rule for Windows Remote Management, and uncheck the Public profile.
- Navigate to:
Computer Configuration -> Policies -> Windows Settings -> Security Settings -> Restricted Groups.- Add a group:
- First textbox: Event Log Readers.
- Under Members of this group, add Network Service.
- Add a group:
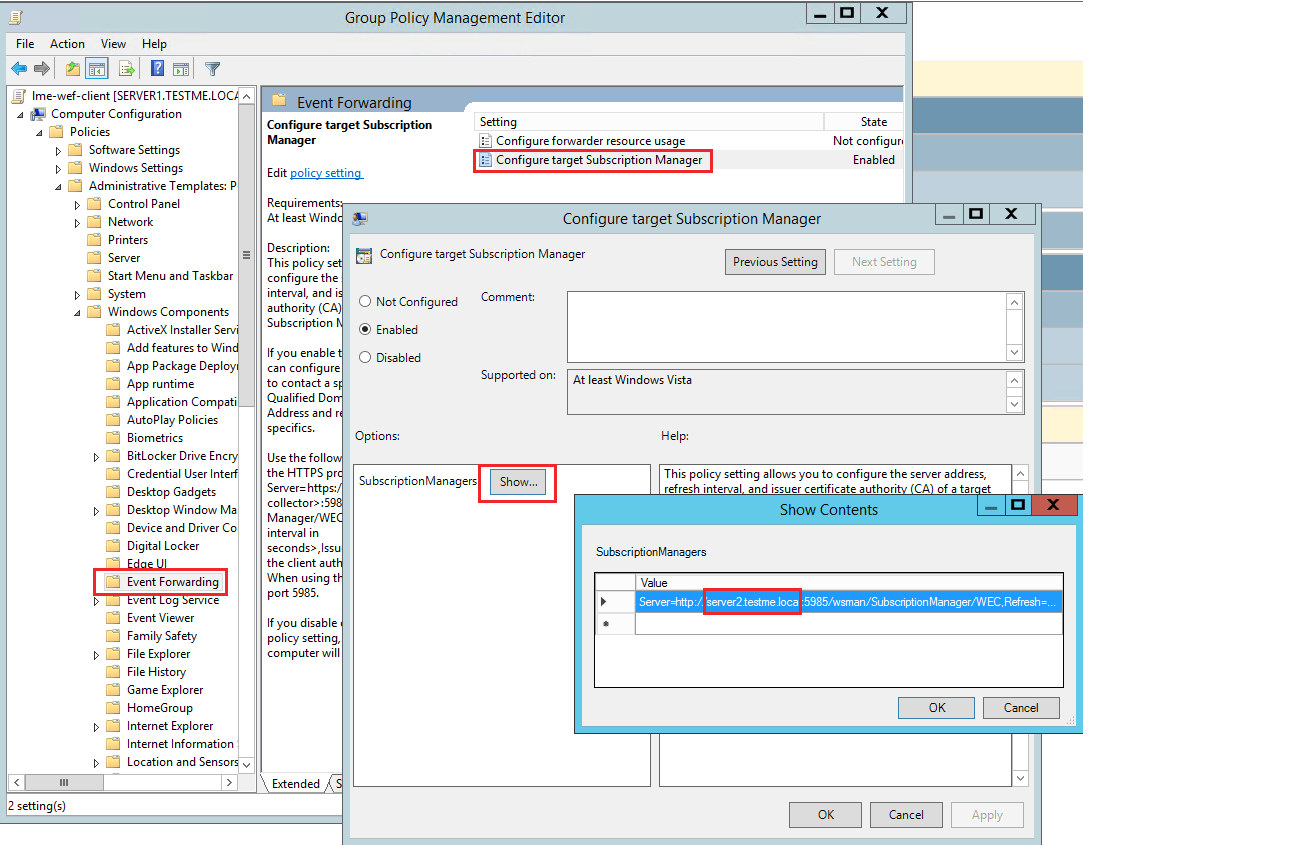
- Navigate to:
Computer Configuration -> Policies -> Administrative Templates -> Windows Components -> Event Forwarding -> Configure target Subscription Manager.- Add a value like:
Server=http://logcollector.yourdomain.com:5985/wsman/SubscriptionManager/WEC,Refresh=900
- Add a value like:
GPO for WinRM Security Hardening
- Name:
GPO_WinRM_Security_Hardening - Purpose: Ensures that WinRM communication is secured and configured to use the best practices for security.
Steps to Create:
- In the GPMC, right-click the root OU or specific OUs for security-sensitive machines, and select Create a GPO in this domain, and link it...
- Name the GPO:
GPO_WinRM_Security_Hardening. - Right-click the new GPO and select Edit.
Configuration:
- Navigate to:
Computer Configuration -> Policies -> Administrative Templates -> Windows Components -> Windows Remote Management (WinRM) -> WinRM Client.- Configure the following settings:
- Allow Basic Authentication: Disabled.
- Allow CredSSP Authentication: Disabled.
- Allow Unencrypted Traffic: Disabled.
- Disallow Kerberos Authentication: Disabled.
- Disallow Negotiate Authentication: Disabled.
- Disallow Digest Authentication: Enabled.
- Trusted Hosts: Disabled.
- Configure the following settings:
- Navigate to:
Computer Configuration -> Policies -> Administrative Templates -> Windows Components -> Windows Remote Management (WinRM) -> WinRM Service.- Configure the following settings:
- Allow Basic Authentication: Disabled.
- Allow CredSSP Authentication: Disabled.
- Allow Remote Server Management through WinRM: Enabled (Restrict IPv4/IPv6 filters to the IP range you are using).
- Allow Unencrypted Traffic: Disabled.
- Disallow Kerberos Authentication: Disabled.
- Disallow Negotiate Authentication: Disabled.
- Disallow WinRM from storing RunAs credentials: Enabled.
- Specify channel binding token hardening level: Enabled (Hardening Level: Relaxed).
- Configure the following settings:
¹ Note: Before rolling out to production, test the GPOs on a pilot set of machines to ensure correct functionality.
Configuring Subscriptions on the WEC Server
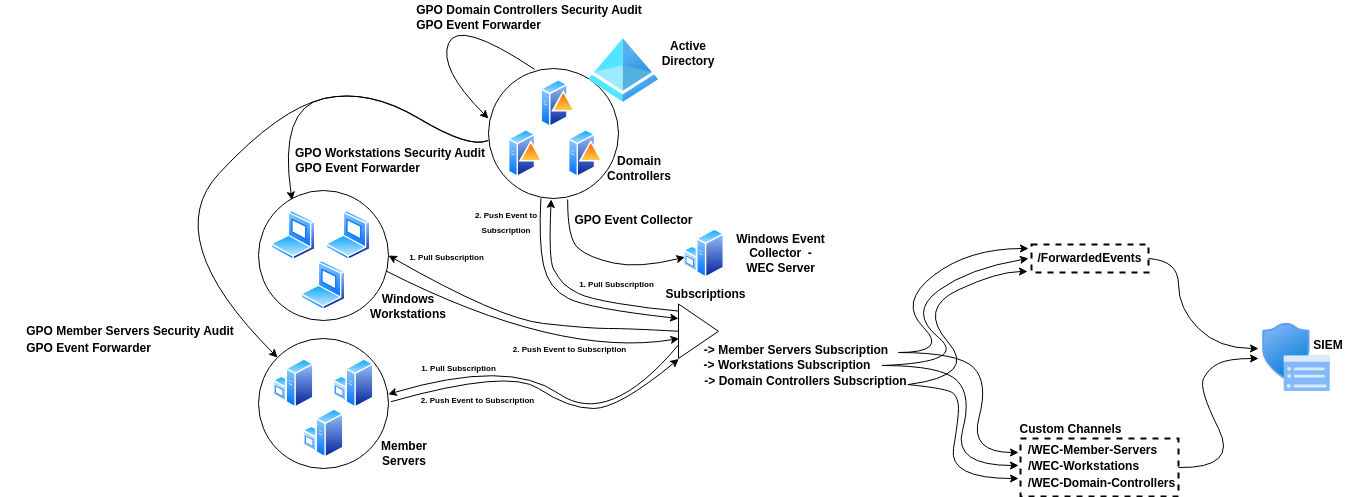
With the GPOs in place, the next step is to create subscriptions on the WEC server. And if you want to segregate the events by source, you can optionally create three custom channels (Member Servers, Domain Controllers, and Workstations) instead of having all the logs in the Forwarded Events channel.
(Optional) Set Up the Custom Event Channels
Using separate channels allows you to set different maximum sizes and rotation strategies for each, tag data uniquely for SIEM ingestion, or assign channels to different disks or storage devices to optimize disk I/O performance.
Please refer to this detailed guide on Creating Custom Windows Event Forwarding Logs.
- Disable the Windows Event Collector Service:
net stop Wecsvc- Unload the current Event Channel file:
wevtutil um C:\windows\system32\CustomEventChannels.man- Copy (and replace) the following files to each WEF server under
C:\Windows\system32:
CustomEventChannels.dll
CustomEventChannels.man- Load the new Event Channel file:
wevtutil im C:\windows\system32\CustomEventChannels.man- Re-enable the Windows Event Collector Service:
net start WecsvcConfigure Subscriptions with Custom Channels on the WEC Server
The next step is to configure event subscriptions to start forwarding logs from clients (e.g., member servers, domain controllers, and workstations) to the WEC server. This process involves creating a subscription that links each group of systems to its corresponding event channel.
- Create a subscription for each group (Member Servers, Domain Controllers, Workstations), in the Event Viewer on the WEC Server and right-click on subscriptions.
- Configure the subscription
- Set the destination log to the corresponding custom channel (WEC-Member-Servers, WEC-Domain-Controllers, or WEC-Workstations).
- Choose either Collector Initiated (WEC server initiates, recommended for smaller environments or where you control the list of systems) or Source Initiated (clients push logs, recommended for larger environments with many dynamic clients as shown on the previous diagram).
- Add source computers for each subscription (Member Servers, Domain Controllers, or Workstations).
- Select Security Events to Forward.
- Advanced Settings: Adjust the event delivery and the heartbeat interval based on your needs.
- Finally, verify events are being forwarded by checking in the channel(s) of the Event Viewer.
Forwarding Logs from WEC to SIEM
Finally, the last step is quite open to you depending on how you want to forward logs collected by the WEC server to your SIEM, you can install tools like NXLog or Winlogbeat on the WEC server.
Resources
- Microsoft Audit Policy Recommendations
- Microsoft: Use Windows Event Forwarding to help with intrusion detection
- Microsoft Appendix L: Events to Monitor
- Microsoft Windows Event Collector
- NXLogs Documentation: Collecting logs from Windows Event Log
- CISA Logging Made Easy
- Installation and configuration for Windows Remote Management
Member discussion