Writing Security Policies for SOC2

Transitioning from ISO27001 certification to SOC2 compliance is a natural progression for many organizations. Whether you've already obtained ISO27001 or have it in your sights, SOC2 is likely on the horizon, being one of the most coveted certifications for demonstrating robust security controls. Chances are, your organization is already fielding inquiries from customers' security compliance teams about SOC2 readiness. And if crafting comprehensive security policies poses a challenge due to limited security governance staff in your security department, I present here a solid base to kickstart your journey towards SOC2 compliance.
StrongDM's Comply: Compliance automation framework
Comply is an open source compliance automation framework, focused on SOC2. The tool includes a collection of pre-authored policies, procedures and narratives that can be easily edited in markdown, has a ticketing integration to allow versioning with GitHub and assign compliance tasks through Jira.
First pull the latest published docker image:
$ docker pull strongdm/comply
From an empty directory that will contain your comply project:
docker run --rm -v "$PWD":/source -p 4000:4000 -it strongdm/comply
Once in the container, you can initiate your project with the comply init command and enter information about your organization and your ticketing system:
root@b5193043befc:/source# comply init
Organization Name: acme inc.
PDF Filename Prefix (no spaces, no trailing separator): acme
✔ SOC2
Comply relies on your ticketing system for optional procedure tracking. You can always come back and enable this integration later.
✔ None
✔ acme inc. Compliance initialized successfully!
Next steps:
* Customize this directory using a text editor ('cat TODO.md' for ideas)
* Try 'comply build' and 'comply serve'
* View output/index.html
* Add this directory to source control
And then build the policies with comply build:
root@b5193043befc:/source# comply build
templates/index.ace -> output/index.html
policies/access.md -> output/acme-AOTP.pdf
policies/application.md -> output/acme-ASP.pdf
...
narratives/system.md -> output/acme-SAN.pdf
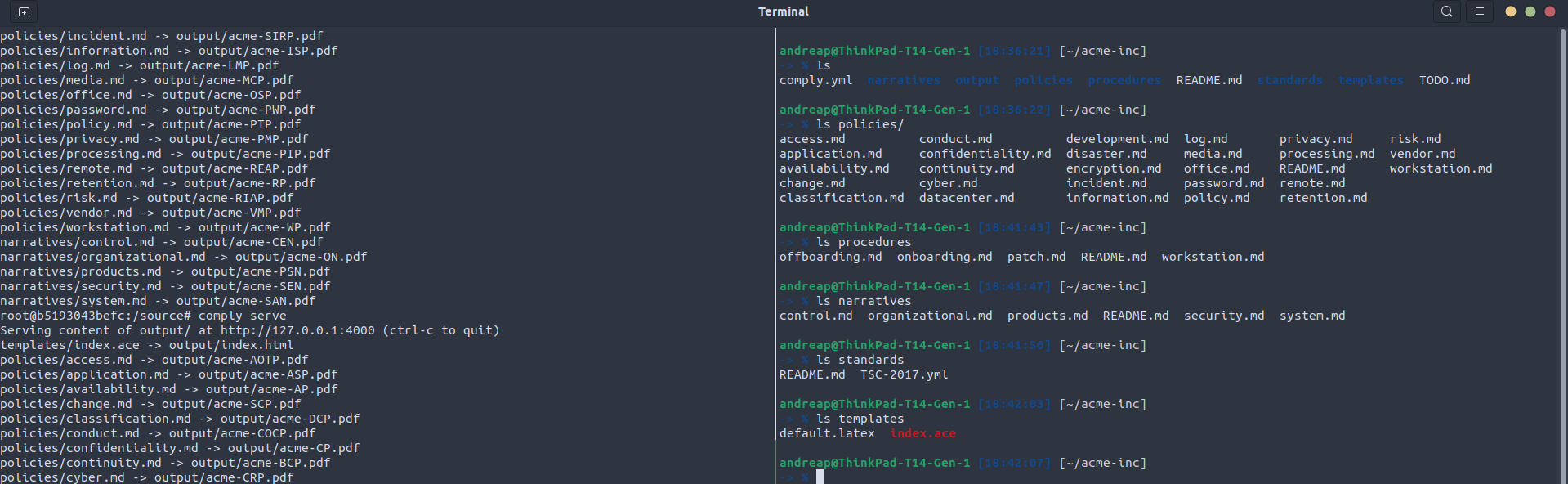
Finally, you can serve the policies on a file server with comply serve:
root@b5193043befc:/source# comply serve
Serving content of output/ at http://127.0.0.1:4000 (ctrl-c to quit)
templates/index.ace -> output/index.html
policies/access.md -> output/acme-AOTP.pdf
policies/application.md -> output/acme-ASP.pdf
...
narratives/system.md -> output/acme-SAN.pdf
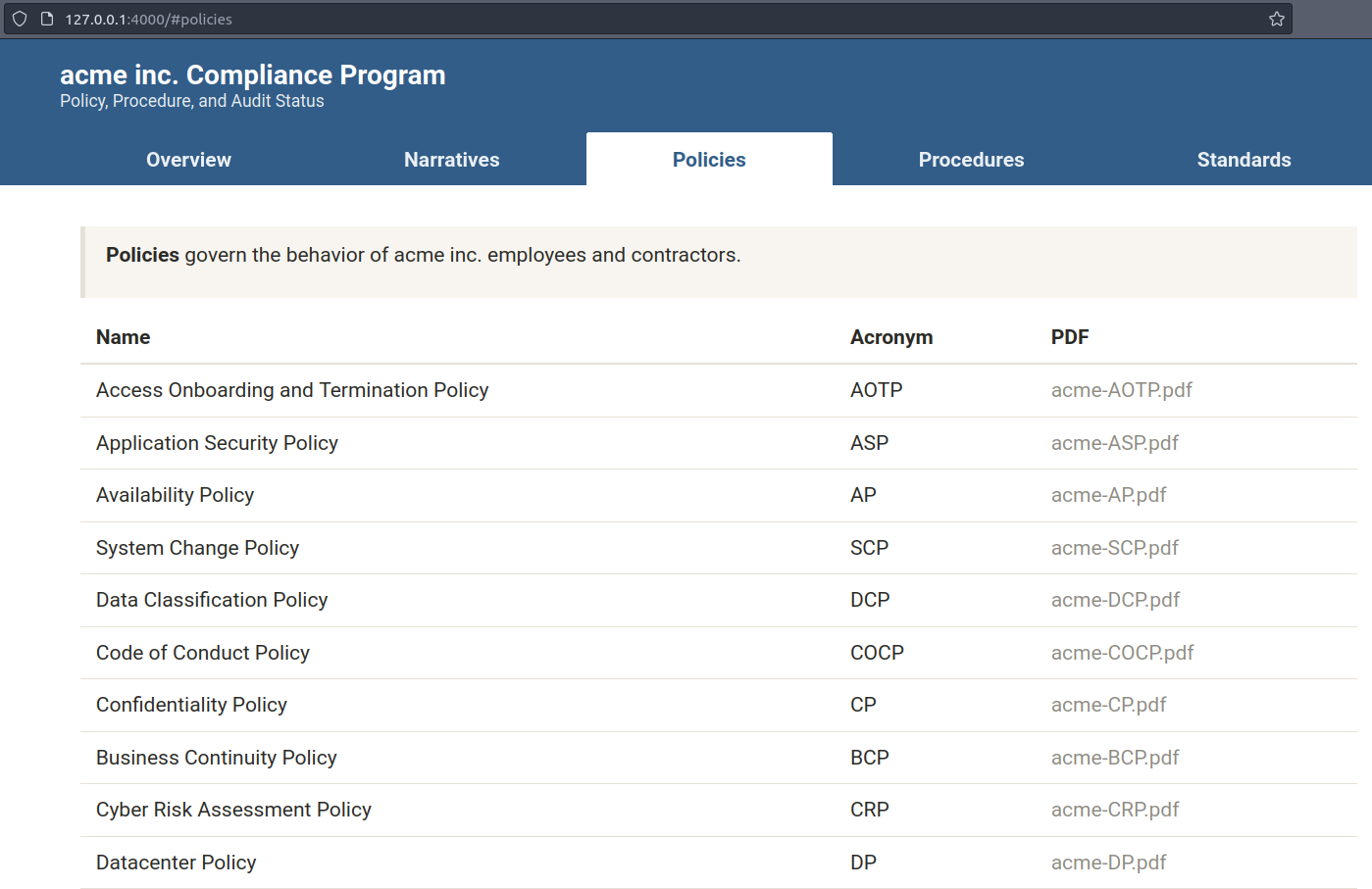
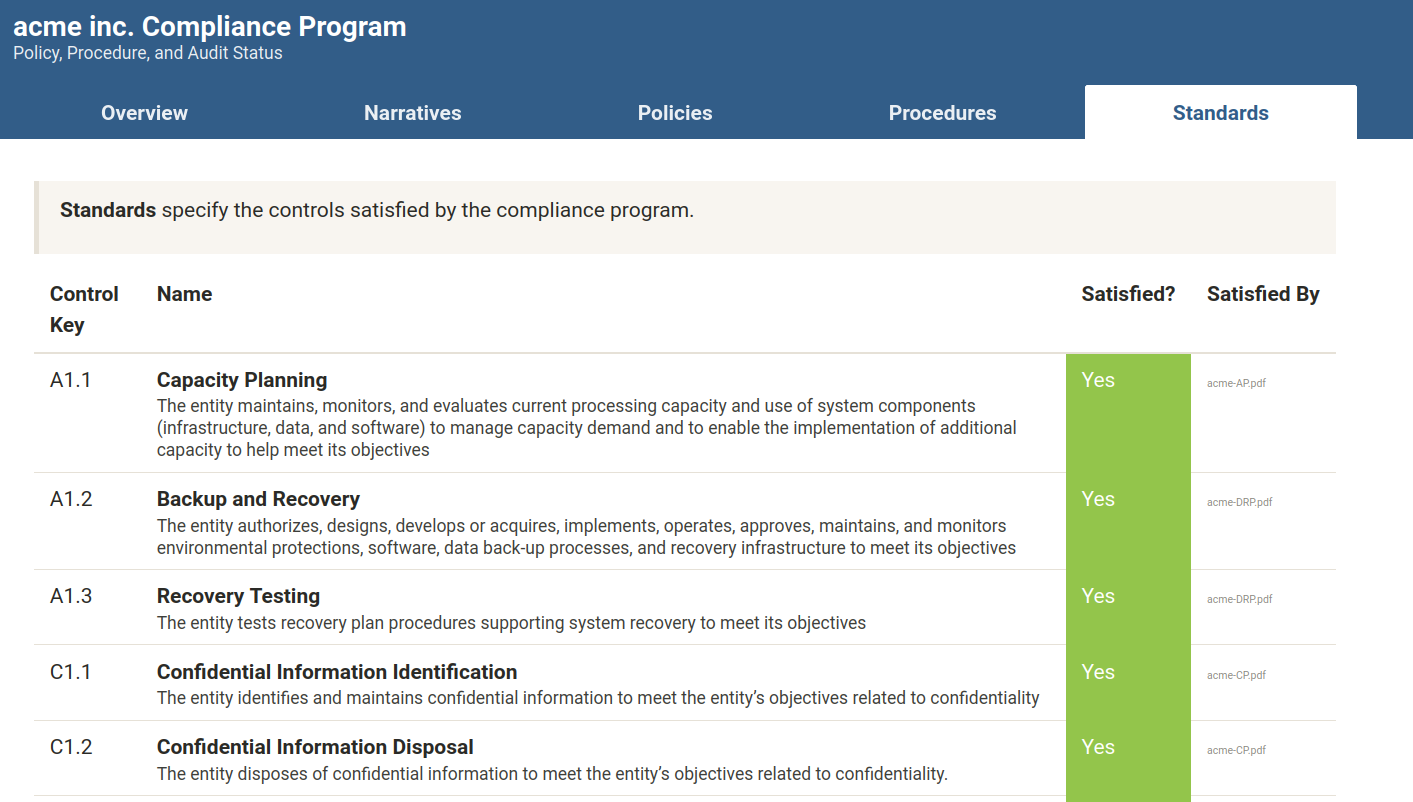
Policies can be easily edited in Markdown and are converted into LaTeX documents and served as PDF under the hood with pandoc.
JupiterOne's Policy Builder
JupiterOne's Policy Builder is a CLI for generating policies, standards and control procedures (PSP) documentation in Markdown and publishing to JupiterOne or Confluence.
First pull the latest published docker image:
$ docker pull jupiterone/pspbuilder
From an empty directory that will contain your project, build the policies:
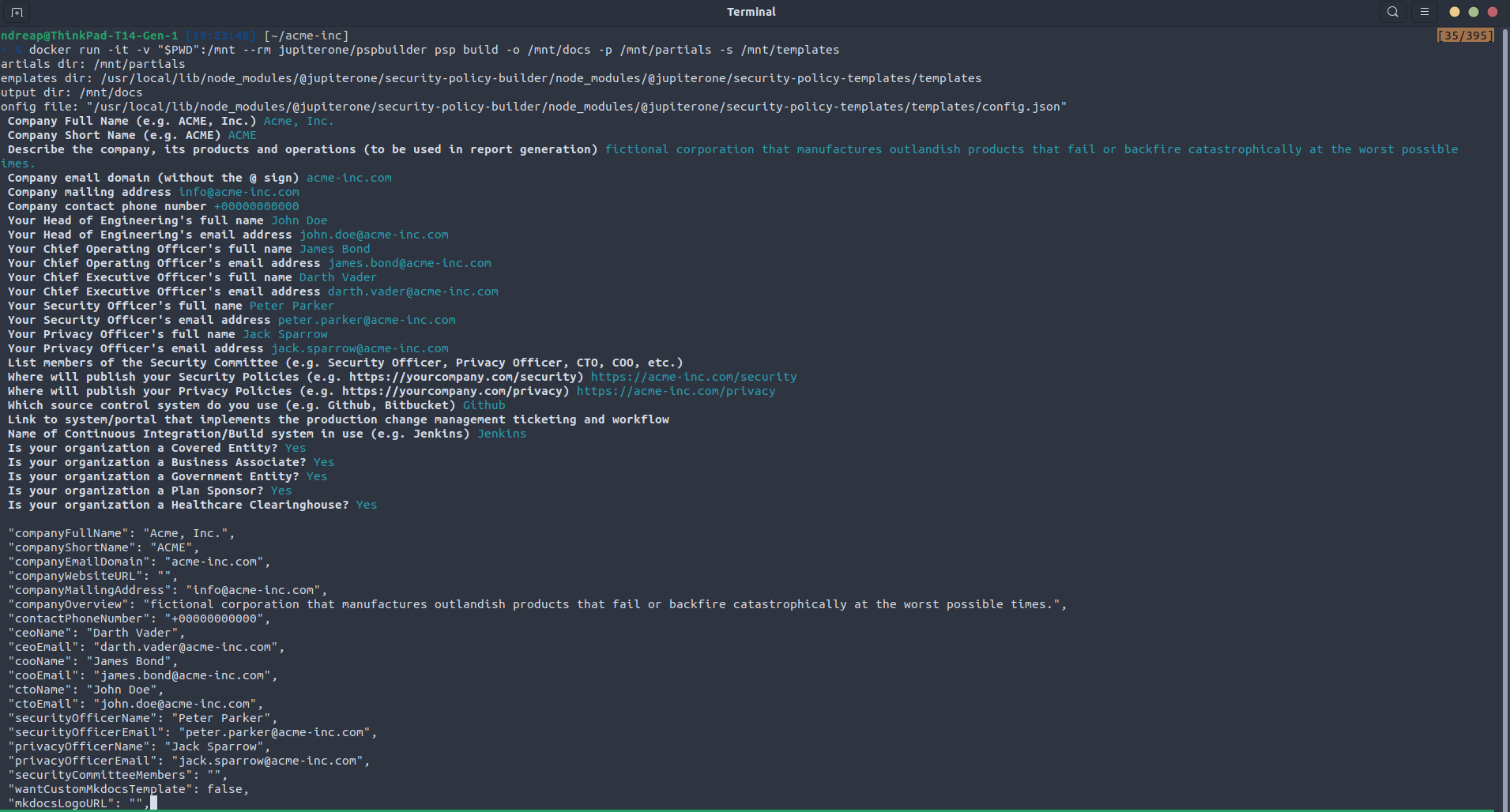
$ docker run -it -v "$PWD":/mnt --rm jupiterone/pspbuilder psp build -o /mnt/docs -p /mnt/partials -s /mnt/templates
and enter information about your organization (company domain, email address, COO, CEO, CISO's full names and email addresses, policies publishing URL, and organization type):
Generate static HTML in 'site' directory (mkdocs command expects the YAML file to be at the root of the project):
$ cp docs/mkdocs.yml . && sed -i "s/pages/nav/g" mkdocs.yml
$ docker run -it -v "$PWD":/mnt --rm jupiterone/pspbuilder mkdocs build -f /mnt/mkdocs.yml
Note: You will have to change 'pages' from mkdocs.yml to 'nav' instead.
You can finally view the static HTML files generated by mkdocs opening http://localhost:8000:
cd site && python3 -m http.server 8000`
SANS Information Security Policy Templates
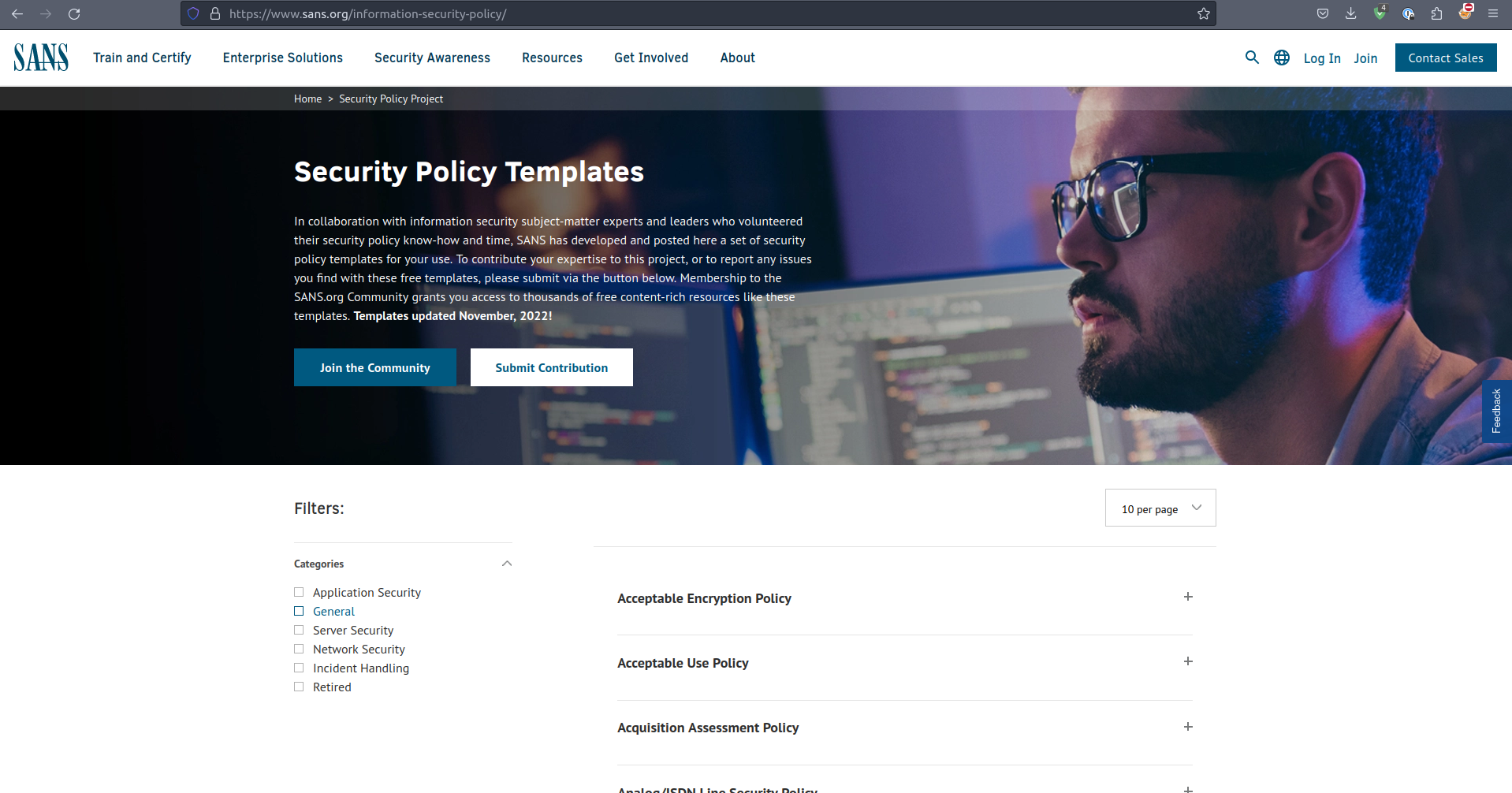
The SANS Information Security Policy Templates are another valuable resource alongside the other policy builders providing a solid base to start writing policies for your company. While not tailored specifically for SOC2 and not providing any publishing function, these templates cover everything for each policy and offer very specific policy, serving as a collaborative effort between SANS and the community. And if you're seeking AI Security Policy templates, note that the last update to these templates occurred in 2022. Therefore, you might need to explore alternative sources for the most recent policies in this domain.
In conclusion, whether using policy builders or not, leveraging templates to initiate SOC2 policy building simplifies the process significantly. There is no point in reinventing the wheel when automation can handle the heavy lifting, allowing focus on tailoring policies to specific organizational needs which is what truly matters. And it's also crucial to consider policy format for ease of maintenance and version tracking. Policy builders offer the advantage of automating policy publication. By adopting this approach, organizations can streamline their compliance efforts while maintaining adaptability to their unique environments.