Automate Compliance and Security Hardening Using OpenSCAP and Ubuntu Security Guide

Compliance as Code
Compliance as Code (CaC) can be simply put as IT security compliance policies written as code. Systems configuration can be audited by these CaC policies to demonstrate your infrastructure's compliance against regulations and industry standards such as CIS Benchmarks, DISA STIG, PCI DSS, HIPAA, and more. Organizations can automate assessment, monitoring and remediation of these compliance controls on various systems with the Security Content Automation Protocol (SCAP) developed by Red Hat and the National Institute of Standards and Technology (NIST).
Introducing OpenSCAP
OpenSCAP is an open-source framework to create security policy content for various platforms — Red Hat Enterprise Linux (RHEL), Fedora, Ubuntu, Debian, SUSE Linux Enterprise Server,... — as well as products — Firefox, Chromium, ...
Writing new rules and maintaining existing security content is simple and easy.
The OpenSCAP Ecosystem

The main tools of the OpenSCAP family that I will present are the following:
- OpenSCAP Base — The oscap cli is used to perform configuration scans on a local system, to validate security compliance content, and to generate reports and guides based on these scans and evaluations. Please note that vulnerability scans are only available for Red Hat products.
- OpenSCAP Daemon — The Daemon is a service that runs in the background making sure your machines are evaluated according to the schedule you specify.
- SCAP Workbench — The Workbench is a benchmarking graphical interface that offers an easy way to perform configuration scans on a single local or a remote system, and perform remediation of the system in accordance with the given XCCDF or SDS file.
- SCAP Security Guide (SSG) — The scap-security-guide package provides the collection of security polices for Linux systems.
OpenSCAP Base
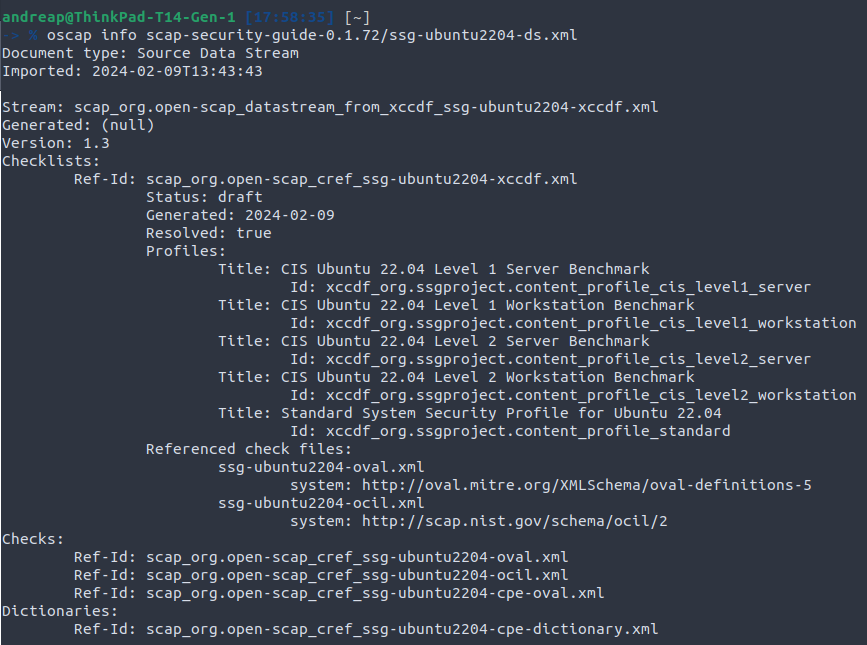
As previously mentioned, with the oscap cli you can audit system configurations with SCAP Security Guides (SSGs).
With commands like oscap info you can gather information about security guide files and oscap xccdf eval you can evaluate compliance against predefined profiles.
oscap info scap-security-guide-0.1.72/ssg-ubuntu2204-ds.xml
oscap xccdf eval --profile xccdf_org.ssgproject.content_profile_standard scap-security-guide-0.1.72/ssg-ubuntu2204-ds.xml --results ssg-ubuntu2204-xccdf-result.xml --report ssg-ubuntu2204-report.html
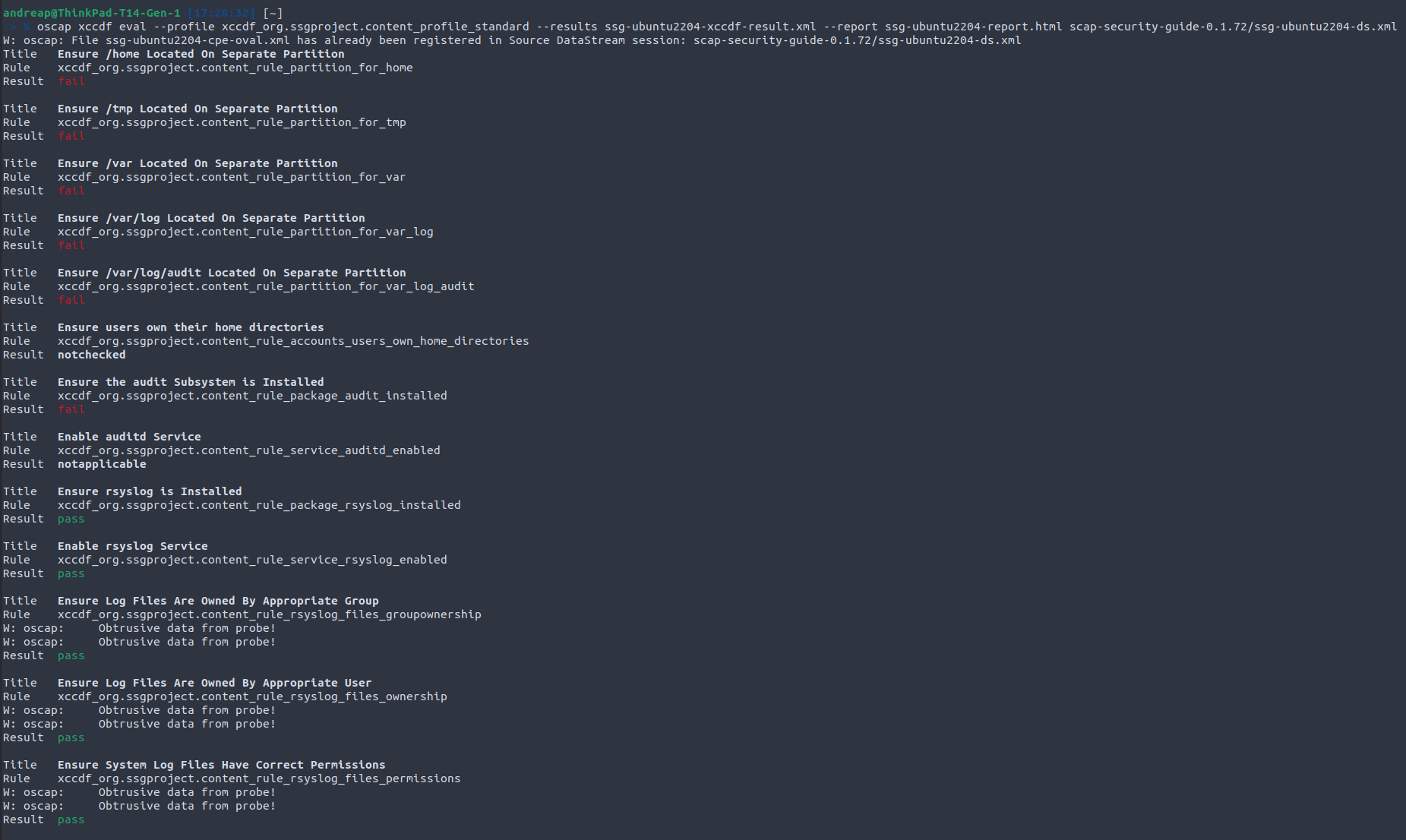
When running the oscap xccdf eval command, the standard output displays your system compliance against each rule if the test is passed or failed and additionally you can generate an HTML report to easily visualize the global scoring with the rules and their severity.
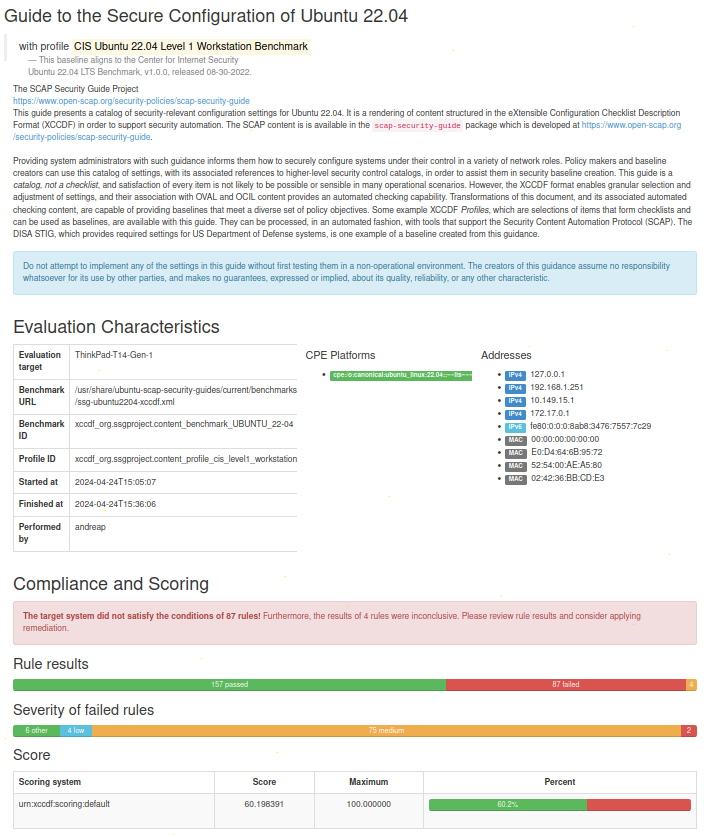
SCAP Workbench
The Workbench brings OpenSCAP to the average user. I highly recommend it as it offers an easy way to perform common oscap tasks such as building tailored profile based on an existing XCCDF profile, running scans, generate remediation scripts and apply remediation.
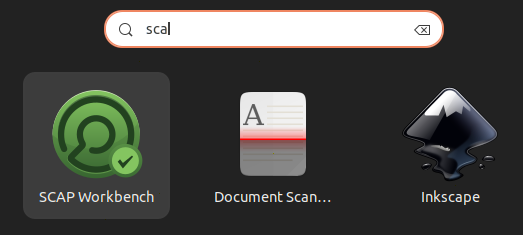
You can select different profiles from a SSG file depending on whether it's a server or a workstation with different set of rules (more or less strict) :
CIS Ubuntu 22.04 Level 1 Server Benchmark (291)CIS Ubuntu 22.04 Level 1 Workstation Benchmark (285)CIS Ubuntu 22.04 Level 2 Server Benchmark (387)CIS Ubuntu 22.04 Level 2 Workstation Benchmark (385)Standard System Security Profile for Ubuntu 22.04 (45)
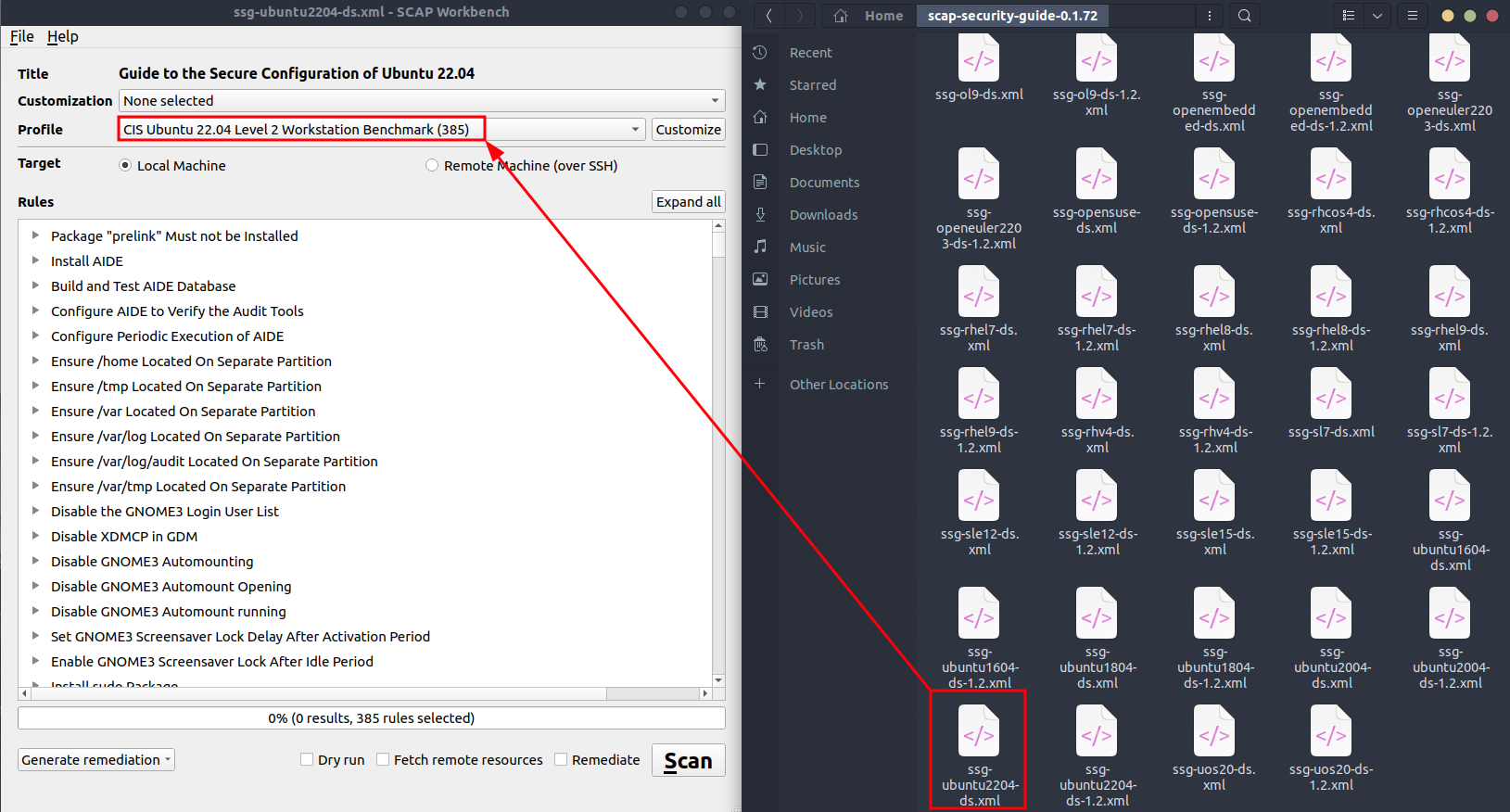
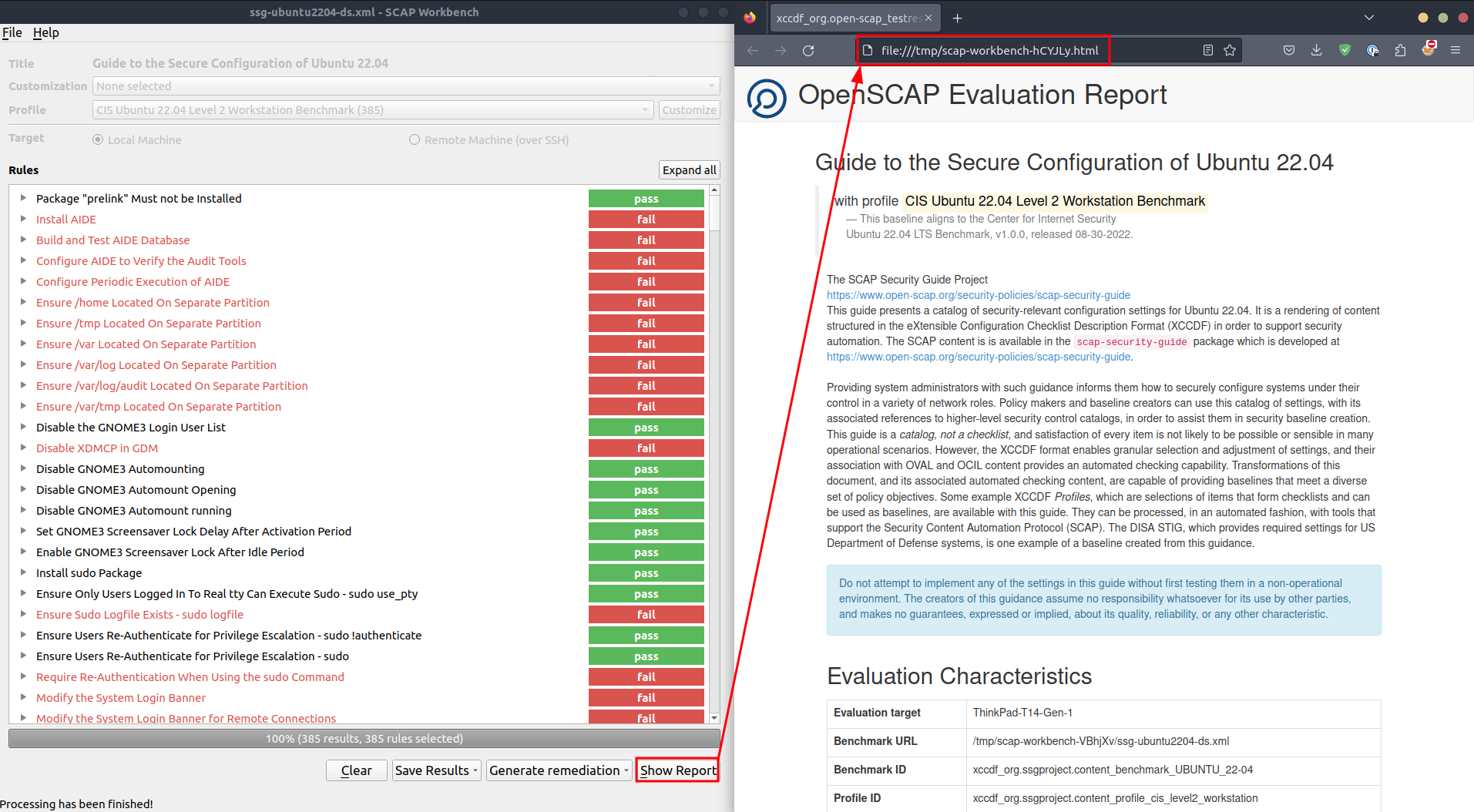
Rules can be grouped by industry standards in the report if you target a specific one for your industry such as PCI-DSS:
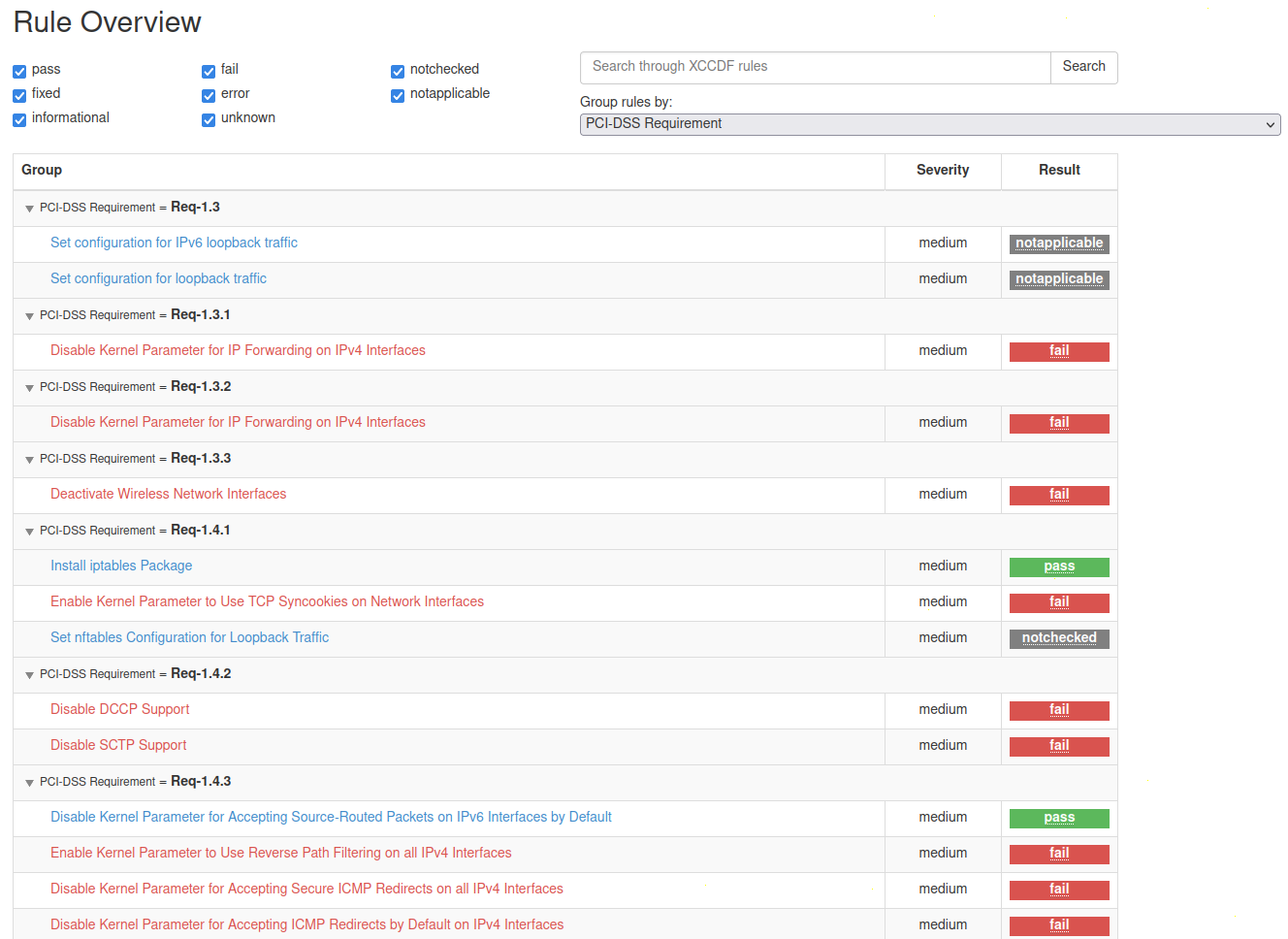
Additionally, you can click on a rule to inspect its content with a link providing an explanatory description of the rule.
Introducing Ubuntu Security Guide
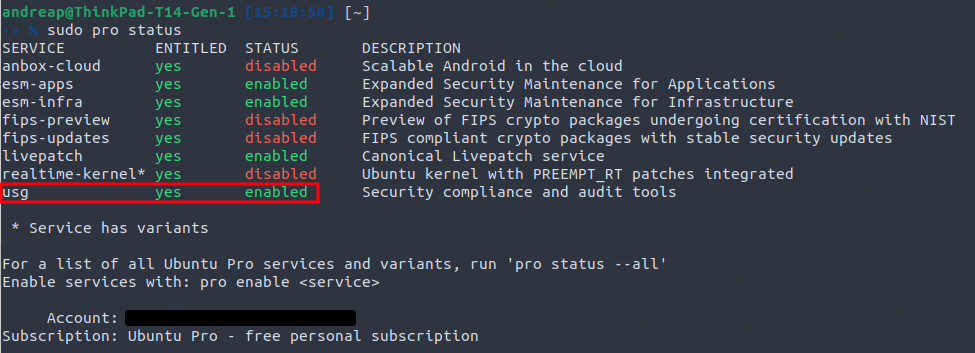
On the other hand, Ubuntu Security Guide (USG) is another tool that makes hardening and auditing with compliance profiles much easier on Ubuntu systems than OpenSCAP, though it uses it as backend. The commands are pretty straightforward to use: audit, generate-fix, fix.
To run USG, you just need to have your machine attached to your Ubuntu Pro subscription (Free up to 5 licenses for personal use):
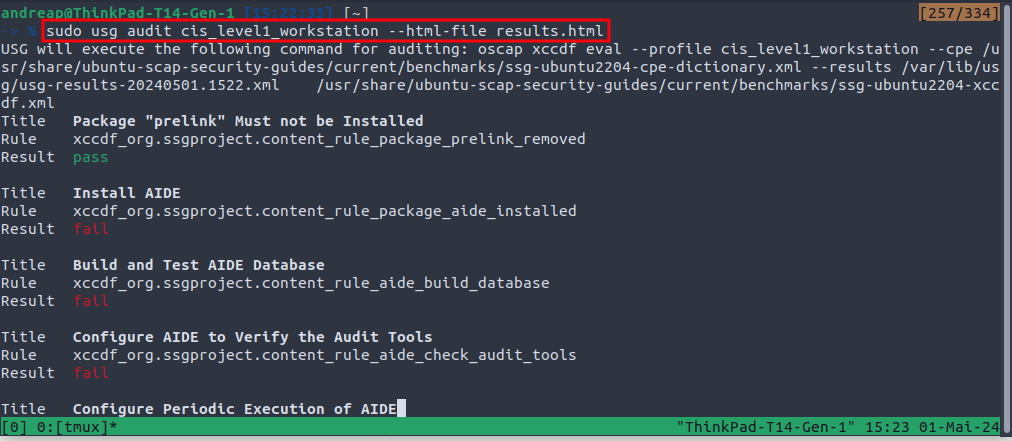
Auditing — You can audit your Ubuntu system for the CIS rules using the following command: sudo usg audit cis_level1_workstation --html-file results.htmlwhich is the equivalent of:
oscap xccdf eval --profile cis_level1_workstation --cpe /usr/share/ubuntu-scap-security-guides/current/benchmarks/ssg-ubuntu2204-cpe-dictionary.xml --results /var/lib/usg/usg-results-20240501.1522.xml /usr/share/ubuntu-scap-security-guides/current/benchmarks/ssg-ubuntu2204-xccdf.xml
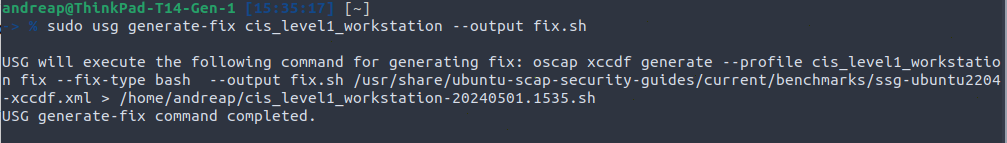
Remediation — You can easily generate a fix with sudo usg generate-fix cis_level1_workstation --output fix.sh or apply it directly sudo usg fix cis_level1_workstation :
Generic Workflow
Leveraging OpenSCAP or USG is not so difficult as you can see, organizations can automate compliance checks and implement security configurations effectively. Here's a summary on how it works:
- Policy Creation: Start by defining security policies based on regulatory requirements, industry standards, or organizational guidelines. These policies outline the security configurations and controls that systems should adhere to.
- Automated Assessment: OpenSCAP allows you to automate the assessment of system configurations against the predefined security policies. It scans the system, identifies deviations from the desired state, and generates detailed reports highlighting areas of non-compliance.
- Remediation: Once areas of non-compliance are identified, the Security Guide provides guidance on implementing necessary security measures to remediate vulnerabilities and align systems with the defined policies. This may involve configuring firewall rules, enabling encryption, or applying access controls, among other actions.
- Continuous Monitoring: Compliance is not a one-time effort but an ongoing process. OpenSCAP Daemon enables continuous monitoring by scheduling regular scans and assessments to ensure that systems remain compliant over time. Any deviations or security risks are promptly identified and addressed.
Benefits of CaC with OpenSCAP and Ubuntu Security Guide
In conclusion, the integration of OpenSCAP or USG to your tooling offers a lot of benefits for organizations seeking to automate compliance:
- Efficiency: Automation streamlines compliance management, reducing the time and resources required for manual assessments and audits.
- Accuracy: Automated scans provide consistent and accurate results, minimizing the risk of human error associated with manual checks.
- Scalability: Compliance as Code allows organizations to scale their compliance efforts across large and dynamic IT environments, ensuring consistency across all systems.
- Adaptability: As security requirements evolve, organizations can easily update and modify security policies to address new threats and regulatory changes.
- Risk Reduction: By proactively identifying and remedying security vulnerabilities, organizations can mitigate the risk of data breaches, cyber attacks, and regulatory penalties.
I highly recommended to couple OpenSCAP with other hardening tools such as AppArmor and SELinux.
Member discussion